Data-link Layer is the second layer of the 7 layers OSI model, which converts frames of data into raw bits for the physical layer and is responsible for framing, flow control, error correction, and retransmission of frames.
MAC addresses are used at this layer, and bridges and network interface cards (NICs) operate at this layer.
The data-link layer establishes and maintains the data link for the network layer above it. It ensures that data is transferred reliably between two stations on the network. A number of protocols can be implemented at this layer depending on whether you are establishing local area network (LAN) or wide area network (WAN) connections between stations.
Data-link protocols are responsible for functions such as addressing, frame delimiting and sequencing, error detection and recovery, and flow control.
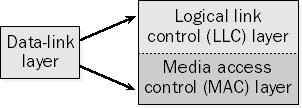
For LANs, the Project 802 standards of the Institute of Electrical and Electronics Engineers (IEEE) separate the data-link layer into two sublayers:
- The logical link control (LLC) layer, the upper of the two layers, which is responsible for flow control, error correction, and resequencing functions for connection-oriented communication, but which also supports connectionless communication
- The media access control (MAC) layer, the lower of the two layers, which is responsible for providing a method for stations to gain access to the medium
Data-Link Layer examples
Examples of data-link protocols for local area networking include the following:
- IEEE 802.3, which provides the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) access method for baseband Ethernet networks
- IEEE 802.5, which provides the token-passing access method for baseband token ring implementations
For WANs, data-link layer protocols encapsulate LAN traffic into frames suitable for transmission over WAN links. Common data-link encapsulation methods for WAN transmission include the following:
- Point-to-point technologies such as Point-to-Point Protocol (PPP) and High-level Data Link Control (HDLC) protocol
- Multipoint technologies such as frame relay, Asynchronous Transfer Mode (ATM), Switched Multimegabit Data Services (SMDS), and X.25
Explore the attacks, vulnerabilities, and exploits that can be found at each one of the seven layers: Hack the Stack: Using Snort and Ethereal to Master The 8 Layers of An Insecure Network (Amazon Store)