The concept of “Admin$” has long been a cornerstone in remote administration for Microsoft Windows environments. While originally designed for older versions like Windows NT and Windows 2000, the Admin$ share continues to be a relevant aspect of remote management and network administration. This special administrative share has evolved to adapt to the security and functionality needs of modern operating systems. In this comprehensive guide, we’ll delve into what Admin$ is, its use cases, security implications, and how it compares to similar mechanisms in Linux systems.
In this article:
- What is Admin$ in Modern Windows Systems?
- Security Implications of Admin$
- Admin$ vs Other Administrative Shares
- How to Enable/Disable Admin$
- Admin$ in a Domain Environment
- Admin$ and Linux: A Comparison
- Conclusion
1. What is Admin$ in Modern Windows Systems?
The Admin$ share is a built-in administrative share that exists in Windows operating systems. While its roots trace back to older versions like Windows NT and Windows 2000, Admin$ continues to be a critical component in the realm of remote administration and management in more contemporary Windows versions such as Windows 10 and Windows Server 2019.
Definition and Purpose
The Admin$ share, by default, points to the %SystemRoot% directory, which is commonly found at C:\Windows in current versions. This special share is created automatically during the OS installation and is hidden, meaning it won’t show up when browsing network shares but can be accessed explicitly if you know it’s there. Its primary purpose is to facilitate remote administration, allowing authorized users to manage system files and settings on the remote computer.
Functionality in Windows 10 and Windows Server 2019
In the context of modern systems like Windows 10 and Windows Server 2019, the Admin$ share operates with increased security measures compared to its predecessors. It still serves the same fundamental function—to enable remote management—but now incorporates enhanced security protocols and permissions. By default, only members of the Administrators group have the privileges to access this share, reinforcing a higher security standard.
Access Control and Authentication
Current versions of Windows integrate the Admin$ share into their broader security model, which includes technologies like Kerberos for authentication. That means, when you attempt to access Admin$ on a remote machine, your credentials are rigorously verified, and the necessary tokens are generated to secure the session. Unauthorized access is usually logged and can trigger alerts depending on the system’s security settings.
Use Cases in Modern Systems
Admin$ is heavily employed in system and network administration tasks, including:
- Software Deployment: Admin$ can be used to push software installations onto remote machines.
- Remote Troubleshooting: System administrators can access logs and system files for diagnostic purposes.
- Script Execution: Administrative scripts can be run remotely, allowing tasks to be automated across multiple systems.
Concluding Thoughts
The Admin$ share is not just a relic of the past; it is an evolving tool adapted to meet the requirements of modern network security and management. Its built-in security features and integration with current Windows operating systems make it a valuable asset for system administrators navigating the complexities of contemporary networked environments.
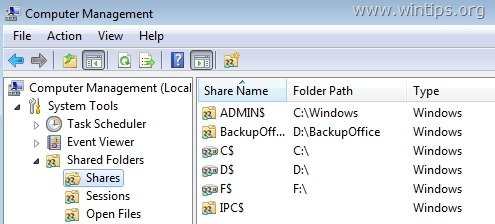
Credits: wintips.org
2. Security Implications of Admin$
Permissions and Access Control
Admin$ is highly restricted, usually available only to members of the Administrators group on a given system. This exclusivity, however, does not completely nullify the security risks associated with its use. Being a prime target for unauthorized users aiming to gain control over a system, Admin$ requires stringent security measures.
Potential Security Risks
- Unauthorized Access: A compromised Administrator account could gain unauthorized access to Admin$, leading to potential data loss, data theft, or unauthorized system changes.
- Malware Propagation: Some malware strains are known to exploit Admin$ to propagate across a network.
- Brute-Force Attacks: Because of its powerful capabilities, Admin$ could be targeted in brute-force attacks aiming to guess the Administrator password.
Best Practices for Securing Admin$
- Strong Password Policy: Always enforce a strong password policy for Administrator accounts.
- Two-Factor Authentication (2FA): If possible, implement 2FA for enhanced security.
- Audit and Monitoring: Keep an eye on the event logs for the Admin$ share and set up alerts for unauthorized access attempts.
- Network Segmentation: Limit the machines that can interact with Admin$, reducing the attack surface.
- Disable If Not Required: If there’s no strong use-case for remote administration via Admin$, consider disabling the Admin$ share.
3. Admin$ vs Other Administrative Shares
Admin$ and Its Specifics
As discussed, Admin$ is geared primarily towards remote administration and maps to the %SystemRoot% directory, usually C:\Windows. It is often leveraged for software deployment and system management tasks.
Other Administrative Shares: C$, D$, etc.
- C$, D$, etc.: These are default shares of the respective drives on a machine. Like Admin$, these are hidden and are accessible only by administrative users.
- IPC$: This is another built-in share used for Inter Process Communication.
Comparing Purposes
- Remote Administration: Admin$ is specifically fine-tuned for system management and remote administration tasks, while C$, D$, and others are more general-purpose drive shares.
- Software Deployment: Admin$ is more often used for deploying software across a network, while C$ and D$ can be used for this purpose but are usually not the first choice.
- Data Access: The drive shares (C$, D$) allow for broader data access and management functionalities compared to Admin$, which is more focused on system files and settings.
When to Use Which
- Use Admin$ for targeted remote administration tasks that need to work directly with system files and settings.
- Use C$ and D$ when you need to manage or retrieve files on specific drives, irrespective of whether they are system files.
Understanding the purpose and limitations of each administrative share can help system administrators make more informed decisions, leading to more effective and secure network management.
4. How to Enable/Disable Admin$
Enabling or disabling the Admin$ share is generally not recommended unless you are certain of the implications. However, for those who need to do so, here’s how you can manage the Admin$ share in modern Windows systems.
Enabling Admin$
- Open Registry Editor: Type
regeditin the Start menu and run the program as an administrator. - Navigate to: Go to
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters - Modify/Add Key: Look for
AutoShareWksfor workstations orAutoShareServerfor server versions. Double-click and set the value to1. If the key does not exist, create a new DWORD value with the aforementioned name. - Restart the Service: Finally, restart the
Serverservice fromServices.mscor by runningnet stop Serverandnet start Serverin the Command Prompt as an administrator.
Disabling Admin$
Repeat the steps above but set the DWORD value to 0 in step 3.
Please, read the article: How to remove administrative shares in Windows Server.
5. Admin$ in a Domain Environment
In an enterprise setting with a domain-controlled network, Admin$ plays a critical role in facilitating centralized administration. Here are some key functionalities:
- Centralized Software Deployment: Admin$ allows for streamlined software deployment across all domain-joined computers.
- Group Policies: Admin$ can be leveraged to enforce Group Policy updates immediately, instead of waiting for the automated refresh cycle.
- Remote Troubleshooting: Allows domain administrators to remotely access a system for troubleshooting without interrupting the user experience.
- Security Audits: Admin$ can be used to execute scripts that perform security audits on domain-joined computers, facilitating compliance with corporate or legal requirements.
6. Admin$ and Linux: A Comparison
Linux systems do not have an equivalent of the Admin$ share by default, but remote administration and file sharing can be achieved using various methods. Here are some:
SSH (Secure Shell)
- Windows Equivalent: Admin$ is often used for remote command execution, a task performed by SSH in Linux.
- Security: SSH is secured with public key cryptography, unlike Admin$ which relies on system-level permissions and optional SMB encryption.
NFS (Network File System)
- Windows Equivalent: Similar to C$ and D$ shares, NFS can share entire filesystems across the network.
- Permission Management: Unlike Admin$, NFS relies on UNIX permissions, offering more granular control over file and directory access.
Samba Shares
- Windows Equivalent: Samba can share Linux directories in a way that is compatible with Windows SMB protocol, making it close to Admin$ in functionality.
- Security: Like Admin$, Samba allows for different layers of access control, from share-level to user-level security.
By understanding the similarities and differences between Linux and Windows remote administration techniques, system administrators can make more informed decisions, particularly in heterogeneous environments.
7. Conclusion
In summary, Admin$ is a powerful tool in Windows for centralized administration, especially in a domain environment. On the flip side, its security implications cannot be ignored. Therefore, understanding how to enable or disable it is crucial. When we turn our gaze to Linux, we find alternatives like SSH and NFS, each with its own pros and cons. Just like Admin$, these tools serve specific needs and come with their own set of security considerations.
Notably, in a mixed environment, it’s beneficial to comprehend both Windows and Linux administrative shares. Ultimately, effective use of Admin$ or its Linux counterparts can significantly streamline network management and elevate security. So, choose wisely and administer smartly.