The world of web hosting is replete with jargon and complex configurations, but understanding these can be the key to efficient and secure website management. Among these, Anonymous Access in IIS (Microsoft Internet Information Services) stands out as a fundamental yet often misunderstood concept.
Have you ever wondered how web content remains readily accessible to a wide array of users without compromising on security? The answer lies in the strategic use of Anonymous Access in IIS. This article delves into the intricacies of Anonymous Access, revealing how it facilitates seamless content delivery while maintaining server integrity.
We will explore the mechanics behind this authentication scheme, its benefits, and its implementation. Whether you’re a budding web administrator or a seasoned IT professional, this piece will provide valuable insights into leveraging Anonymous Access for optimal server performance.
In this article:
- What is Anonymous Access in IIS?
- Setting Up Anonymous Access
- Advantages and Limitations
- Case Studies
- Troubleshooting Common Issues
- Conclusion
- References

1. What is Anonymous Access in IIS?
Anonymous Access is one of three authentication schemes for Microsoft Internet Information Services (IIS).
It is a fundamental authentication scheme designed to streamline user access to web content. It operates by allowing users to interact with web applications or websites without the need for explicit user identity verification. Essentially, when a user requests access to a site, IIS processes this request using a predefined anonymous user account. This method is particularly useful for public-facing websites where user-specific data or personalized interaction is not required.
The core of Anonymous Access lies in its simplicity and efficiency. By removing the barrier of user authentication, it facilitates quicker and broader access to web content, making it an ideal choice for websites aiming for maximum reach and accessibility.
Comparison with Other Authentication Schemes
Unlike Anonymous Access, other IIS authentication schemes, such as Basic, Digest, Windows (integrated), and Forms-based authentication, require some form of user identity verification. For instance, Basic authentication prompts users for a username and password, transmitting credentials in base64 encoding. While easy to implement, it is less secure unless paired with a secure protocol like HTTPS.
Windows authentication, on the other hand, is more secure and integrates seamlessly with Windows server environments, using NTLM or Kerberos protocols. It’s best suited for intranet sites where users are part of the same Windows domain.
In comparison, Anonymous Access bypasses these complexities, making it the go-to choice for public websites that don’t require personalized user data. However, it’s essential to balance ease of access with security considerations, a point we will explore in the next chapter.
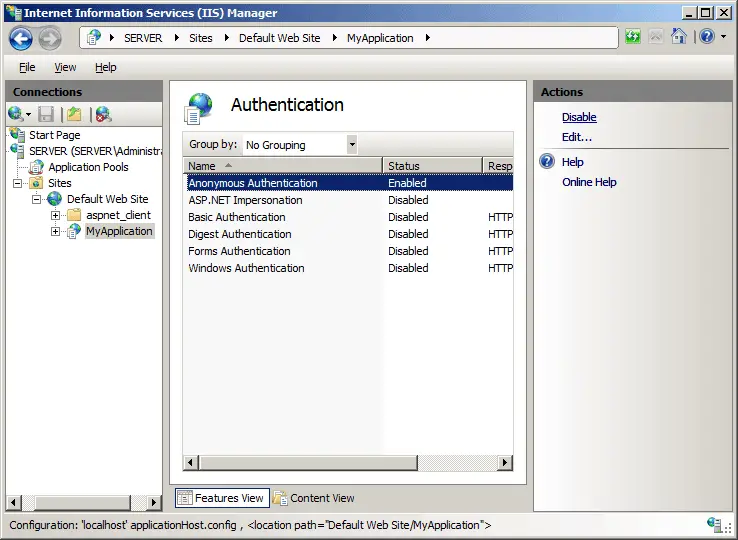
2. Setting Up Anonymous Access in IIS
Step-by-Step Guide
- Open IIS Manager: Start by launching the IIS Manager on your server.
- Select Your Website: In the connections pane, navigate to the website for which you want to enable Anonymous Access.
- Open Authentication Settings: From the website’s home pane, double-click on the “Authentication” feature.
- Enable Anonymous Authentication: In the Authentication pane, you’ll find various authentication methods. Right-click on “Anonymous Authentication” and select “Enable”.
- Configure User Identity (Optional): By default, IIS uses a built-in account. However, you can specify a custom user account by selecting “Edit” under Anonymous Authentication.
Best Practices and Security Considerations
While setting up Anonymous Access is straightforward, it’s crucial to implement best practices to maintain server security:
- Use Specific User Accounts: Instead of the default IIS account, consider using a specific user account with limited privileges. This reduces potential damage in case of a security breach.
- Regularly Update IIS: Keep your IIS server updated with the latest security patches and updates.
- Monitor Traffic: Regularly monitor your website for unusual traffic patterns or requests, which could indicate a security issue.
- Secure Sensitive Content: Ensure that sensitive areas of your website are not accessible via Anonymous Access. Use more secure authentication methods for these parts.
- Implement HTTPS: While not directly related to authentication, using HTTPS encrypts data between the server and the client, adding an extra layer of security.
In summary, Anonymous Access in IIS offers a straightforward approach to web content accessibility. When implemented with consideration to security, it provides an efficient way to serve public content while keeping the server secure.
3. Advantages and Limitations
Benefits of Using Anonymous Access
Anonymous Access in Microsoft IIS offers several distinct advantages:
- Ease of Use: It simplifies the user experience by eliminating login barriers, making it ideal for public websites.
- Reduced Server Load: By bypassing user authentication processes, it lowers the server’s workload, enhancing performance.
- Accessibility: Ensures that content is accessible to all users, crucial for public information and service websites.
- Quick Setup: Anonymous Access is straightforward to configure, saving time and effort for administrators.
Potential Risks and How to Mitigate Them
However, this ease of access comes with potential risks:
- Vulnerability to Attacks: Without user authentication, sites are more susceptible to unauthorized access and malicious activities.
- Limited User Tracking: It’s challenging to track user behavior or preferences, which can be a drawback for personalized content delivery.
Mitigation Strategies:
- Secure Sensitive Data: Restrict Anonymous Access to only public areas of your website.
- Regular Monitoring: Implement robust monitoring tools to detect and respond to suspicious activities promptly.
- Layered Security Approach: Combine Anonymous Access with other security measures like firewalls and intrusion detection systems.
4. Case Studies
Real-World Applications and Scenarios
- Public Information Portal: A government website implemented Anonymous Access to provide public health information. The site successfully handled increased traffic during a health crisis, demonstrating the efficiency of Anonymous Access in high-demand scenarios.
- E-commerce Platform: An e-commerce site initially used Anonymous Access for its product pages. However, it faced challenges in personalizing user experiences. The site then restricted Anonymous Access to public pages while implementing user-specific authentication for personalized areas like user accounts and checkout processes.
Lessons Learned
- Balancing Accessibility and Personalization: Anonymous Access is ideal for broad reach but may limit personalization options.
- Security is Paramount: Even for public content, maintaining strong security practices is essential to protect against data breaches and unauthorized access.
- Flexibility in Implementation: Combining Anonymous Access with other authentication methods can optimize both user experience and security.
These case studies illustrate that while Anonymous Access is a powerful tool in the IIS arsenal, its effective use requires a balanced approach, considering both the needs of the audience and the security of the platform.
5. Troubleshooting Common Issues
Identifying and Resolving Typical Problems
- Access Denied Errors: This often occurs when the anonymous user account doesn’t have proper permissions. Ensure that the account has read access to the content.
- Server Performance Issues: If you notice slowdowns, check if high traffic to anonymously accessed pages is causing resource strain. Implement caching strategies to alleviate this.
- Security Alerts: Regularly encountering security warnings can indicate misconfigurations. Review and tighten security settings, ensuring only necessary content is available via Anonymous Access.
Expert Tips
- Regular Audits: Conduct frequent audits of your IIS configuration to ensure compliance with best practices.
- Log Analysis: Keep a close eye on server logs. Unusual patterns can be early indicators of problems.
- Keep Software Updated: Always update IIS and related software to the latest versions to avoid known vulnerabilities.
6. Conclusion
In this article, we’ve explored the nuances of Anonymous Access in IIS, highlighting its advantages, such as ease of use and accessibility, and its limitations, particularly concerning security. We’ve also discussed real-world applications, emphasizing the importance of a balanced approach to using Anonymous Access effectively.
Final Thoughts and Recommendations
Anonymous Access is a powerful feature when used correctly. It’s essential to balance its convenience with robust security measures. Regular monitoring, updates, and a careful configuration approach are key to leveraging its benefits while minimizing risks.
7. References
- “Microsoft Internet Information Services (IIS) 7.0 Resource Kit” by Mike Volodarsky et al.
- RFC 2616 – Hypertext Transfer Protocol — HTTP/1.1
- “Professional IIS 7” by Kenneth Schaefer et al.
- IIS.net – Official Microsoft IIS Site for Documentation and Resources