In the vast universe of network security and data management, proxies play a significant role. Among them, the Application Layer Proxy stands out due to its specific operation and benefits. This article will unravel the layers behind this proxy, aiming to equip System Administrators, Network Engineers, and Computer Science majors with the knowledge they need to navigate this tool effectively.
Before diving deep into the Application Layer Proxy, let’s refresh our understanding of proxies. A proxy, in essence, acts as an intermediary that forwards requests from clients to other servers and returns the server’s response back to the clients.
In this article:
- What is an Application Layer Proxy?
- How Does It Work?
- Benefits of Using an Application Layer Proxy
- Drawbacks and Considerations
- Application Layer Proxy vs. Packet Filtering
- Real-world Use Cases
- Setting Up an Application Layer Proxy
- Frequently Asked Questions
- Conclusion
- References

1. What is an Application Layer Proxy?
An Application Layer Proxy, also known as an Application Proxy, is a proxy server that operates at the application layer (Layer 7) of the OSI model. Unlike a simple packet forwarder, this proxy understands the application’s protocol it’s working with, be it HTTP, FTP, or any other.
For example, in Microsoft Proxy Server, the Web Proxy Service is an application layer proxy for the Hypertext Transfer Protocol (HTTP), Secure Hypertext Transfer Protocol (S-HTTP), File Transfer Protocol (FTP), and Gopher protocols. Application layer proxies provide security by hiding internal network addresses from the outside world.
Application layer proxies provide more support for the additional capabilities of each protocol than do circuit layer proxies. For example, application layer proxies can support virus scanning. Application layer proxies are also client-neutral and require no special software components or operating system on the client computer to enable the client to communicate with servers on the Internet using the proxy server.
Microsoft Proxy Server can grant users access to selected application layer protocols and can restrict access to remote Web sites by domain name, IP address, and subnet mask.
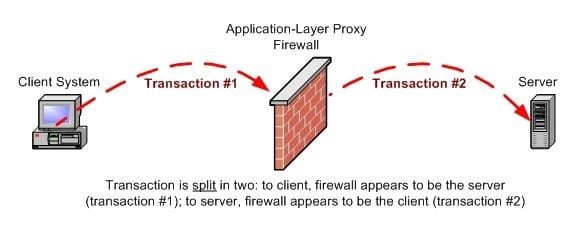
2. How Does It Work?
An Application Layer Proxy doesn’t merely act as a forwarding service; it actively participates in the communication between the client and the server.
- Interception and Inspection: When a client initiates a request, the proxy intercepts this request. At this point, the proxy reads and interprets the request’s data because it understands the application protocol being used.
- Connection Establishment: Rather than simply passing on the client’s request, the proxy establishes its own connection to the destination server. This means the server sees the request coming from the proxy, not the original client.
- Data Transmission: Once connected, the proxy sends the client’s request to the server. The server then processes the request and sends the response back to the proxy.
- Response Handling: The proxy receives the server’s response, inspects it for any defined criteria (like banned content or potential threats), and then sends the appropriate data back to the client.
- Termination: After the data transfer is complete, the proxy effectively closes two connections: one with the client and one with the server.
3. Benefits of Using an Application Layer Proxy
Application Layer Proxies offer a multitude of advantages, especially in terms of security and control:
- Enhanced Security:
- Deep Packet Inspection (DPI): This feature allows the proxy to inspect data packets’ contents, helping in identifying and blocking malicious content.
- Content Filtering: Not only can harmful content be blocked, but organizations can also filter out non-work-related sites or specific keywords.
- Granular Control:
- Protocol-Specific Rules: Since the proxy understands specific application protocols, administrators can create rules tailored to specific services, like blocking FTP transfers while allowing HTTP requests.
- User-Based Access: Pairing with authentication mechanisms, these proxies can restrict or allow content based on user identity.
- Performance Boost:
- Caching: By storing frequently accessed data, these proxies can serve client requests without contacting the destination server, speeding up response times.
- Load Balancing: Some advanced proxies can distribute client requests across multiple servers, ensuring no single server is overwhelmed.
- Authentication and Privacy:
- User Verification: Before accessing specific resources, users might be required to authenticate, ensuring only authorized individuals gain access.
- Privacy Shield: Since the server sees the request coming from the proxy and not the client, user privacy is maintained.
4. Drawbacks and Considerations
While there are numerous benefits, it’s also essential to be aware of potential limitations and considerations:
- Latency Issues:
- Deep Inspection Delays: The very feature that boosts security — deep packet inspection — can also introduce delays as each packet is thoroughly examined.
- Complex Configuration:
- Advanced Knowledge Required: Setting up and maintaining an Application Layer Proxy requires a deeper understanding of application protocols. Improper configurations can lead to security gaps or service interruptions.
- Higher Resource Consumption:
- CPU Intensive: The intricate tasks of inspecting and interpreting application data can be taxing on the proxy server’s resources.
- Memory Usage: Caching, while beneficial for speed, can consume a significant amount of memory, especially if not managed correctly.
- Compatibility Issues:
- Protocol Limitations: If the proxy doesn’t understand a specific application protocol, it might not handle the data correctly, leading to potential service issues.
5. Application Layer Proxy vs. Packet Filtering
Understanding the distinction between an Application Layer Proxy and Packet Filtering is pivotal for network professionals. Let’s shed light on the primary differences:
- Depth of Inspection:
- Application Layer Proxy: Provides deep packet inspection (DPI), examining the data within the packet itself. It interprets protocol-specific commands and can make granular decisions based on content. This allows for more sophisticated filtering rules.
- Packet Filtering: Operates at a more superficial level. It bases decisions on source and destination IP addresses, port numbers, and the protocol used, without a deeper understanding of the data inside the packet.
- Performance:
- Application Layer Proxy: Due to its deeper inspection and two-step connection process, it can introduce more latency compared to simple packet filtering.
- Packet Filtering: Typically offers faster performance as it only examines the packet headers and doesn’t engage in a detailed analysis of the content.
- Security:
- Application Layer Proxy: Generally considered more secure due to its in-depth packet analysis, capability to block specific application commands, and user-level access controls.
- Packet Filtering: While it can block potentially harmful traffic based on IP, port, and protocol, it lacks the depth to recognize and block more sophisticated threats present in the payload.
- Flexibility:
- Application Layer Proxy: Offers a greater degree of flexibility, allowing for protocol-specific rules, content caching, and more.
- Packet Filtering: Has a more straightforward approach, focusing on allowing or blocking traffic based on basic criteria.
6. Real-world Use Cases
Application Layer Proxies are widely used across various scenarios. Here are some real-world applications:
- Web Content Filtering in Schools and Enterprises:
- Educational institutions and businesses employ Application Layer Proxies to filter out distracting or inappropriate web content, ensuring that the network is used for its intended purpose.
- Secure Web Gateways:
- Organizations use these proxies as part of their secure web gateways to scan outgoing and incoming web traffic for threats, blocking malicious websites or content.
- E-commerce Transaction Safety:
- E-commerce platforms utilize these proxies to inspect transaction data, ensuring that fraudulent activities are minimized.
- Load Balancing for High-traffic Websites:
- High-traffic web services like streaming platforms or online gaming sites deploy Application Layer Proxies to distribute incoming traffic across multiple servers, ensuring optimal performance.
- Remote Access and VPN:
- Businesses use these proxies in combination with VPN services to give remote employees secure access to internal resources, inspecting the traffic for potential security threats.
- Email Security:
- Application Layer Proxies can be set up to inspect incoming and outgoing email traffic, filtering out spam, phishing attempts, or malicious attachments.
7. Setting Up an Application Layer Proxy
Setting up an Application Layer Proxy is a multi-step process tailored to ensure optimal security and functionality. Here’s a simplified guide for those aiming to implement one:
- Identify the Need: Understand the specific requirement for the proxy. Do you need content filtering, improved security measures, or load balancing? Defining the purpose will guide the subsequent setup steps.
- Choose the Right Software: Numerous software solutions are available, both open-source (like Squid) and commercial (like F5’s BIG-IP). Research and select the one that best fits your requirements.
- Hardware Considerations: Depending on the expected traffic load and the software’s recommendations, ensure you have the right hardware setup. Remember, processing at the application layer can be resource-intensive.
- Network Configuration:
- IP Addressing: Decide whether you want a transparent setup (where users don’t know they’re being proxied) or non-transparent (users must set up their devices to use the proxy).
- Port Selection: Determine which ports the proxy will listen on. Typically, web proxies listen on port 80 or 443 but can be configured for others.
- Define Rules and Policies: This is where the real power of an Application Layer Proxy comes into play. Set up rules for content filtering, URL blocking, MIME type restrictions, etc. Tailor the rules based on the organizational or personal needs.
- Testing: Before deploying the proxy fully, run it in a test environment. Ensure it behaves as expected, processes requests correctly, and adheres to the defined rules.
- Monitoring and Maintenance: Once deployed, continuously monitor the proxy’s performance. Regularly update the software to incorporate security patches and new features.
8. Frequently Asked Questions
- Is an Application Layer Proxy suitable for all organizations?
- While beneficial, it might be overkill for small organizations with minimal network traffic.
- How does it differ from a Transparent Proxy?
- A Transparent Proxy redirects client requests without modifying them or requiring any extra client configuration.
- Can it protect against all cyber threats?
- While it offers robust security, no tool can guarantee 100% protection. Layered security measures are always recommended.
- Does it impact network speed significantly?
- There might be a slight delay due to deep packet inspection, but modern proxies are optimized to minimize this lag.
- Are there any free Application Layer Proxy tools available?
- Yes, Squid is a popular open-source option.
9. Conclusion
For professionals in the tech industry, understanding the nuances of an Application Layer Proxy is crucial. Not only does it offer enhanced security measures, but it also provides better control over network traffic. Whether you’re a seasoned Network Engineer or a budding Computer Science student, harnessing the power of this proxy can be a game-changer for your operations and projects.