AXFR Request is a type of Domain Name System (DNS) request in which a secondary DNS server requests the update of information from a master DNS server. An AXFR request always results in a full zone transfer.
This can take time and use considerable network bandwidth if the zone files are large. An alternative to AXFR is the incremental zone transfer protocol described in Request for Comments (RFC) number 1995.
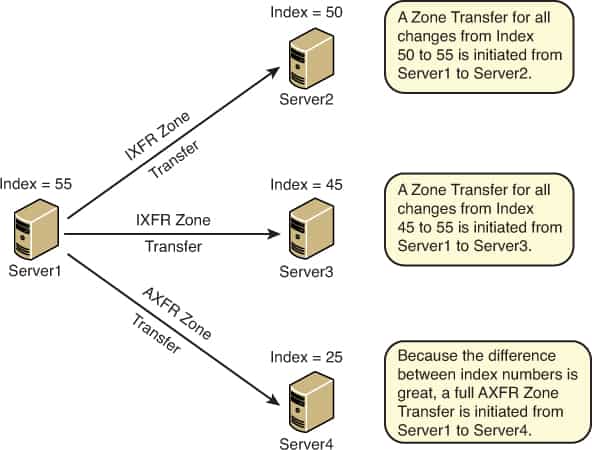
Incremental zone transfers use an IXFR request and transfer only those portions of the zone file that have been changed. Incremental zone transfers are supported by the DNS service running on the Microsoft Windows Server family.
AXFR stands for Asynchronous Full Transfer Zone (DNS request).
What is the difference between AXFR and IXFR?
The current full zone transfer mechanism (AXFR) is not an efficient means to propagate changes to a small part of a zone, as it transfers the entire zone file. Incremental transfer (IXFR) as proposed is a more efficient mechanism, as it transfers only the changed portion(s) of a zone.
DNS Zone Transfer AXFR Requests May Leak Domain Information
On April 13, 2015, CISA (Cybersecurity & Infrastructure Security Agency) released an alert (TA15-103A) stating that DNS Zone Transfer AXFR Requests may leak domain information.
A well-known problem with DNS is that zone transfer requests can disclose domain information; for example, see CVE-1999-0532 and a 2002 CERT/CC white paper. However, the issue has regained attention due to recent Internet scans still showing a large number of misconfigured DNS servers. Open-source, tested scripts are now available to scan for possible exposure, increasing the likelihood of exploitation. The impact is that a remote unauthenticated user may observe internal network structure, learning information useful for other-directed attacks.
Solution
Configure your DNS server to respond only to zone transfer (AXFR) requests from known IP addresses. Many open-source resources give instructions on reconfiguring your DNS server. For example, see this AXFR article for information on testing and fixing the configuration of a BIND DNS server.
In other words, in order to prevent this vulnerability from occurring, the DNS server should be configured to only allow zone transfers from trusted IP addresses. The following is an example of how this can be accomplished in the BIND DNS server. Additionally, it’s also recommended to use transaction signatures (TSIG) for zone transfers to prevent IP spoofing attempts.