Know what it means Certificate Services on Windows Server, from Network Encyclopedia.
What is Certificate Services?
Certificate Services is a service running on a Windows server operating system that receives requests for new digital certificates over transports such as RPC or HTTP. It checks each request against custom or site-specific policies, sets optional properties for a certificate to be issued, and issues the certificate. Certificate Services allows administrators to add elements to a certificate revocation list (CRL), and to publish signed CRLs on a regular basis.

Windows Active Directory Certificate Services (AD CS)
Since Windows Server 2008, Certificate Services are managed inside Active Directory. This tool allows network administrators to issue and manage public-key certificates.
Basically what this means is rather than going to a third-party Certificate Authority (CA) to get PKI certificates and using their hosted services, you can actually handle this in-house.
Benefits of Using Active Directory Certificate Services (AD CS)
Using AD CS provides a number of benefits, mostly around certificate administration.
- Pull from Active Directory – You can use the existing endpoint identity information that exists in AD to register for certificates (to avoid re-registering).
- Leverage Existing Group Policy – You can configure AD Group Policies to dictate which users and machines are allowed which types of certificates.
- Automate Certificate Provisioning and Lifecycle Management – Once an endpoint comes online for the first time, a request is sent to AD to check which certificate types (called templates) the endpoint has access based on the Group Policy. Based on the results of that request, the endpoint requests the appropriate certificates, which are then sent back to the endpoint and installed. Certificates can be set to automatically renew, eliminating the worry over unexpected expiration and gaps in coverage.
- Silent Installation – As hinted above, the installation process is automatic and doesn’t require any end-user (or IT) intervention.
Disadvantages of Running Your Own CA
Public-Key Infrastructure, because it’s a complex technical subject, brings additional considerations. Here are just a few examples:
- Hardware Costs – You need to protect and store your root and signing private keys on secure hardware (e.g. Hardware Security Module).
- Maintaining Validation Services – You need to ensure you have a way to check certificate validity, such as updating CRLs, keeping CRLs and running OCSP services.
- Internal PKI Expertise – PKI is complex and best practices are continually evolving. How will you ensure you maintain compliance?
Certificate Services Features
Certificate Services allows an organization to manage the issuing, renewal, and revocation of certificates. It has a number of features which make it valuable to organizations that do not choose to rely upon external certification authorities and who need a flexible tool that can be adapted to the needs of the organization.
- Active Directory integration
- Adherence to standards: Certificate Services accepts standard PKCS #10 requests and issues X.509 3.0 certificates. Certificate Services works with non-Microsoft clients and browsers, and non-Microsoft web servers.
- Application Uses: Certificate Services issues certificates that can be used in public key infrastructure (PKI) applications.
- Extensible framework: Certificate Services supports X.509 certificate extensions.
- Hardware cryptography support: Certificate Services supports hardware-related cryptography, such as issuing certificates stored on smart cards.
- Hierarchy support: A CA hierarchy consists of a top-level CA (called the Root CA) with one or more subordinate CAs which have been issued certificates by the root CA. A possible CA hierarchy scenario would be in an organization with one root CA, which was used to issue certificates to several subordinate CAs.
- Policy independence information: Certificates are granted according to policies that define criteria that requesters must meet to receive a certificate.
- Request support: Certificate Services supports certificate requests based on the PKCS #10 format and the Keygen (Netscape) format. Certificate Services also supports PKCS #7 renewal requests and Cryptographic Message Syntax (CMS) requests.
- Transport independence information: Certificate Services accepts certificate requests from an applicant through HTTP, DCOM, RPC, disk file, or by custom transport. Certificate Services posts certificates to the applicant through HTTP, DCOM, RPC, disk file, or custom transport.
Installing Certificate Services
In Windows Server 2003, Certificate Services 2.0 can be installed from Control Panel by clicking Add or Remove Programs and then clicking Add/Remove Windows Components to install or uninstall Certificate Services.
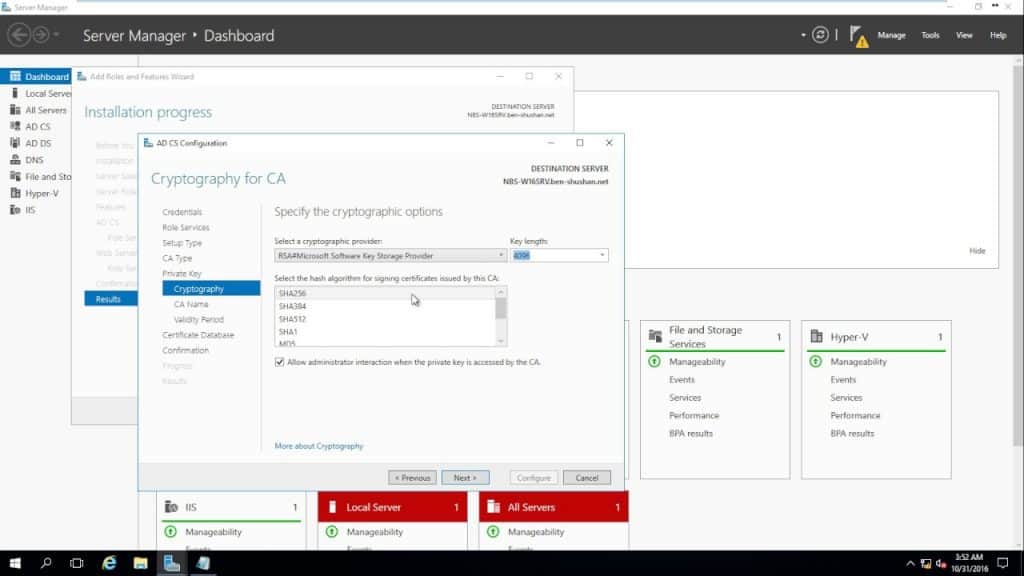
On recent versions of Windows Server follow these steps:
- Log on as a member of both the Enterprise Admins group and the root domain’s Domain Admins group.
- In Server Manager, click Manage, and then click Add Roles and Features. The Add Roles and Features Wizard opens.
- In Before You Begin, click Next. (The Before You Begin page of the Add Roles and Features Wizard is not displayed if you have previously selected Skip this page by default when the Add Roles and Features Wizard was run.)
- In Select Installation Type, ensure that Role-Based or feature-based installation is selected, and then click Next.
- In Select destination server, ensure that Select a server from the server pool is selected. In Server Pool, ensure that the local computer is selected. Click Next.
- In Select Server Roles, in Roles, select Active Directory Certificate Services. When you are prompted to add required features, click Add Features, and then click Next.
- In Select features, click Next.
- In Active Directory Certificate Services, read the provided information, and then click Next.
- In Confirm installation selections, click Install. Do not close the wizard during the installation process. When the installation is complete, click Configure Active Directory Certificate Services on the destination server. The AD CS Configuration wizard opens. Read the credentials information and, if needed, provide the credentials for an account that is a member of the Enterprise Admins group. Click Next.
- In Role Services, click Certification Authority, and then click Next.
- On the Setup Type page, verify that Enterprise CA is selected, and then click Next.
- On the Specify the type of the CA page, verify that Root CA is selected, and then click Next.
- On the Specify the type of the private key page, verify that Create a new private key is selected, and then click Next.
- On the Cryptography for CA page, keep the default settings for CSP (RSA#Microsoft Software Key Storage Provider) and hash algorithm (SHA2), and determine the best key character length for your deployment. Large key character lengths provide optimal security; however, they can impact server performance and might not be compatible with legacy applications. It is recommended that you keep the default setting of 2048. Click Next.
- On the CA Name page, keep the suggested common name for the CA or change the name according to your requirements. Ensure that you are certain the CA name is compatible with your naming conventions and purposes because you cannot change the CA name after you have installed AD CS. Click Next.
- On the Validity Period page, in Specify the validity period, type the number and select a time value (Years, Months, Weeks, or Days). The default setting of five years is recommended. Click Next.
- On the CA Database page, in Specify the database locations, specify the folder location for the certificate database and the certificate database log. If you specify locations other than the default locations, ensure that the folders are secured with access control lists (ACLs) that prevent unauthorized users or computers from accessing the CA database and log files. Click Next.
- In Confirmation, click Configure to apply your selections, and then click Close.