In an era where digital security is paramount, Certificate Revocation Lists (CRLs) stand as a critical line of defense in maintaining the integrity and trust of digital communications. As cyber threats escalate and digital interactions become more complex, the importance of CRLs has never been greater. Essentially, a CRL is a list of digital certificates that have been revoked by a Certificate Authority (CA) before their scheduled expiration dates, due to compromise or other issues. These lists play a vital role in the public key infrastructure (PKI), acting as sentinels to prevent fraudulent or unauthorized use of digital certificates.
In this article, we’ll explore the ins and outs of CRLs – their definition, historical evolution, and their indispensable role in today’s digital security landscape.
Table of Contents:
- Understanding CRLs in Digital Security
- The Role of Certificate Authorities in CRL
- Certificate Revocation List in Public Key Infrastructure (PKI)
- The CRL Process: From Creation to Replication
- Implementing CRLs in Windows Server
- Advanced Topics in Certificate Revocation List
- Conclusion
- References

1. Understanding CRLs in Digital Security
Definition and Basic Concept
A Certificate Revocation List is essentially a digital ‘no-fly list’ for certificates. It contains serial numbers of certificates that are no longer trustworthy. When a certificate is revoked, it’s akin to declaring a passport invalid; it cannot be used to verify identity or establish secure communications. In the realm of PKI, where certificates are the bedrock of digital identities, the CRL is a fundamental tool for ensuring that only valid and secure certificates are in circulation.
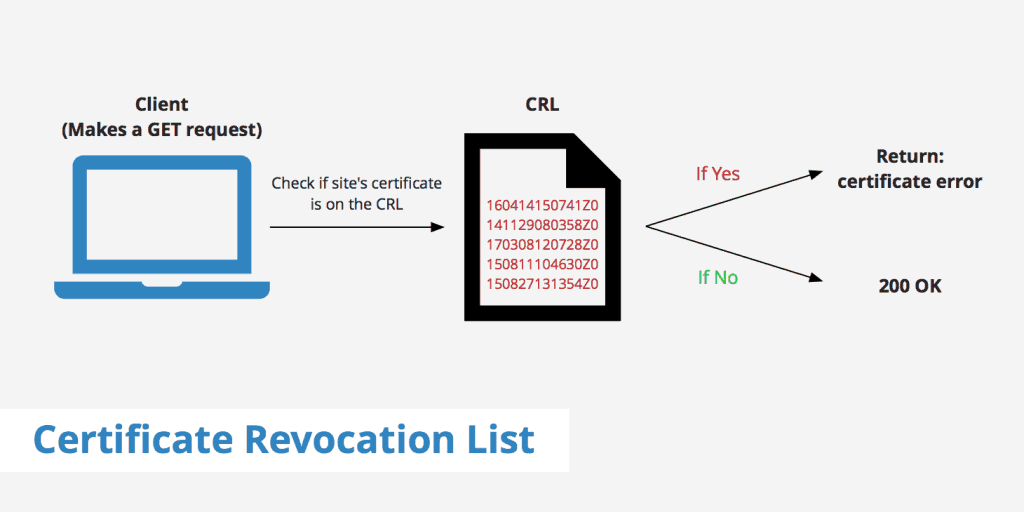
Historical Context and Evolution
The concept of CRLs has evolved significantly since its inception. Initially, CRLs were a straightforward, albeit cumbersome, solution to the problem of certificate revocation. In the early days of digital security, the management of these lists was a manual and time-intensive task. However, as the internet and digital communications grew, so did the scale and complexity of managing CRLs. This evolution brought about more sophisticated methods of distribution and management, such as delta CRLs and the use of Online Certificate Status Protocol (OCSP). These advancements have made it possible to manage the growing number of digital certificates and their revocations more efficiently, ensuring that the PKI remains a robust framework for digital trust.
2. The Role of Certificate Authorities in CRL
How CAs Manage and Update CRLs
Certificate Authorities (CAs) play a pivotal role in maintaining CRLs. They are responsible for tracking and revoking certificates that are compromised, expired, or no longer valid for various reasons. This process involves a rigorous validation to ensure that the revocation is warranted. Once a certificate is deemed invalid, the CA updates the CRL, adding the certificate’s serial number to the list. This update process is periodic, ensuring that the Certificate Revocation List remains current and reliable.
Public Availability and Access
CAs ensure that CRLs are publicly accessible. They are typically hosted on a publicly accessible repository or a distribution point, often via a URL provided within the certificate itself. This accessibility allows users and systems to verify the revocation status of a certificate in real-time, an essential aspect of maintaining trust in digital communications. The transparency and availability of CRLs are key to their effectiveness in sustaining a secure digital environment.
3. CRL in Public Key Infrastructure (PKI)
Integration with PKI Systems
In the PKI framework, CRLs are integrated as a core component for validating certificates. When a system or application encounters a digital certificate, it refers to the Certificate Revocation List to check if the certificate has been revoked. This check is a critical step in establishing a secure connection or validating a digital signature. The integration of CRLs into PKI systems underscores their importance in verifying the authenticity and integrity of digital certificates.
CRLs vs Other Revocation Mechanisms
While CRLs are a traditional method for certificate revocation, other mechanisms like the Online Certificate Status Protocol (OCSP) offer alternatives. OCSP provides real-time validation of a certificate’s status, which can be more efficient than downloading and parsing a CRL. However, CRLs are still widely used due to their simplicity and broad support across systems. Understanding the strengths and limitations of each method is key in choosing the right approach for a specific application or environment within PKI.
4. The CRL Process: From Creation to Replication
Steps in Creating a Certificate Revocation List
The creation of a Certificate Revocation List involves several key steps:
- Identification of Revoked Certificates: Certificate Authorities (CAs) identify certificates that need revocation due to various reasons, such as compromise, expiration, or specific request.
- Updating the List: The identified certificates’ serial numbers are added to the CRL. This list also includes the revocation date and reason.
- Signing the CRL: The updated CRL is then digitally signed by the CA to ensure its integrity and authenticity.
- Publication: The signed CRL is published to a designated repository or distribution point, making it accessible for verification purposes.
Distribution and Replication Challenges
The distribution and replication of CRLs can pose challenges, primarily due to their size and the frequency of updates. Large CRLs can be cumbersome to distribute and manage, especially in environments with limited bandwidth. Additionally, ensuring timely replication across various points to reflect the most recent revocations is critical. Overcoming these challenges often requires a balanced approach between update frequency and distribution methodologies.
5. Implementing CRLs in Windows Server
Specifics for Windows Server 2003 and 2016
- Windows Server 2003: It introduced Certificate Services, allowing administrators to add revoked certificates to the Certificate Revocation List and publish updated lists regularly. It was a step forward in managing PKI elements within the Windows environment.
- Windows Server 2016: This version advanced CRL management with Active Directory Certificate Services (AD CS). It provided enhanced features for enrolling and managing certificates, including more efficient CRL handling.
Best Practices for Administrators
For effective CRL management in Windows Server environments, administrators should:
- Regular Updates: Ensure the CRL is regularly updated and published to reflect the current revocation status of certificates.
- Optimize Distribution: Utilize efficient distribution methods to manage the size and accessibility of the Certificate Revocation List, especially in larger networks.
- Monitor and Audit: Regularly monitor the CRL for integrity and perform audits to ensure it aligns with security policies and compliance requirements.
- Educate Users: Inform users about the significance of Certificate Revocation List checks and the role of PKI in maintaining a secure digital environment.
6. Advanced Topics in CRL
Overcoming Common CRL Challenges
- Scalability: Implementing scalable solutions like delta CRLs, which only contain changes since the last full CRL, to manage large volumes of data efficiently.
- Timeliness: Adopting automated systems for regular updates to ensure CRLs are current and relevant.
- Integration: Streamlining CRL integration with existing security systems for cohesive security management.
Future of CRL in Cybersecurity
- Technological Advances: Exploring advancements like blockchain for decentralized and tamper-evident CRLs.
- Enhanced Protocols: Leveraging newer protocols like OCSP Stapling to improve efficiency in certificate status checking.
- AI Integration: Utilizing AI and machine learning for predictive analysis and proactive revocation.
7. Conclusion
Certificate Revocation Lists are a cornerstone in the edifice of digital security. They ensure that revoked certificates are recognized and invalidated, maintaining the trustworthiness of digital communications. For IT professionals, understanding the intricacies of CRLs is paramount in navigating the complexities of cybersecurity. The key takeaways include the critical role of CAs in managing CRLs, the integration of CRLs in PKI, and the emerging technologies shaping the future of CRLs.
8. References
- “Digital Identity” by Phillip J. Windley
- “PKI and Certificate Security” by Brian Komar
- “Network Security Essentials” by William Stallings
- Articles from the Journal of Cybersecurity and Digital Trust
- Technical resources from the Internet Security Research Group (ISRG)