The term “Global Address List” (GAL) is commonly associated with Microsoft Exchange, serving as a centralized directory of all email addresses in a specific network. However, the concept has broader implications across various computing and networking environments. In this updated article, we aim to peel back the layers of GAL to explore its multi-faceted applications in the computer networking sphere. We will delve into its functionalities, configurations, and importance in different contexts, transcending its traditional role in Microsoft Exchange.
In this article:
- What is the Global Address List (GAL)?
- Types of Global Address Lists
- Configurations and Settings
- Interoperability
- Security Aspects
- Use Cases
- Best Practices
- Emerging Trends
- Conclusion
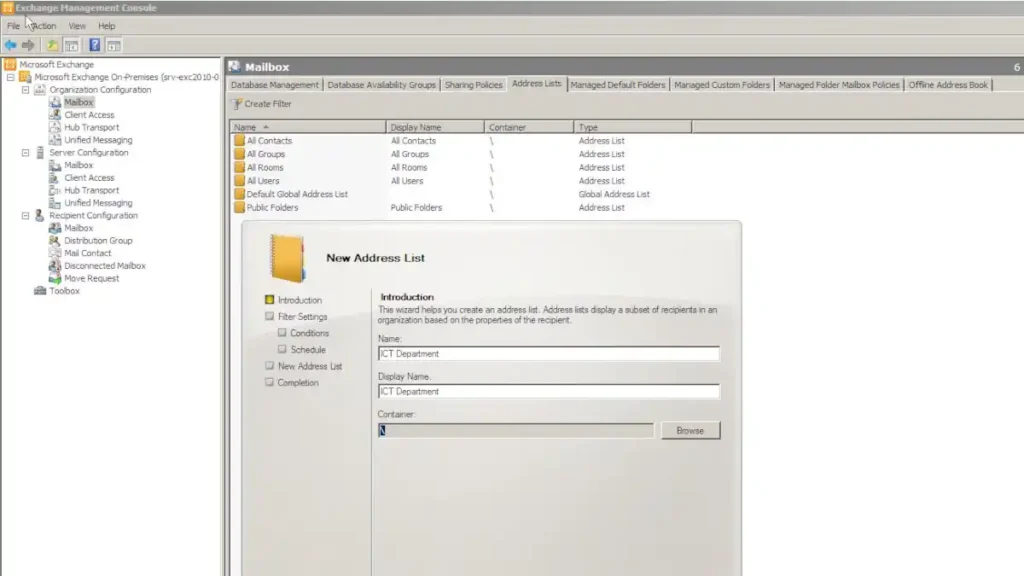
1. What is the Global Address List (GAL)?
In the context of Microsoft Exchange and Outlook, the Global Address List (GAL) serves as a cornerstone feature. Essentially, it’s a centralized directory or repository containing information about users, groups, distribution lists, and other resources within an organization’s Exchange environment. Typically managed by IT administrators, the GAL in Exchange makes it easier for users to find and communicate with one another without having to keep track of individual email addresses or phone numbers. It auto-populates in the Outlook client, offering a seamless experience for end-users. Moreover, it can be tailored to display custom attributes, such as job titles or departments, further enhancing its utility.
Generalized Concept in Computing and Networking
Beyond the Microsoft ecosystem, the term ‘Global Address List’ can take on a broader meaning. In generic computing and networking environments, a GAL can refer to any centralized directory that maintains a list of users, devices, or resources within a particular network or domain. Whether it’s an LDAP (Lightweight Directory Access Protocol) server or a cloud-based directory service, the primary function remains the same: to facilitate easy access to and management of network resources. In essence, it acts as the “Yellow Pages” of a network, providing a single point of reference for various entities to find and connect with each other.
In summary, while the term ‘Global Address List’ may be most commonly associated with Microsoft Exchange and Outlook, its importance and utility span across various computing platforms and networking configurations. Its purpose—to centralize and simplify access to network resources—stands as a universal need in today’s interconnected world.
2. Types of Global Address Lists
The concept of a Global Address List (GAL) is not exclusive to any one environment or platform. Over time, its implementations have diversified to meet various requirements and technological frameworks. In this chapter, we’ll delve into the primary types of GALs, discussing their features, use-cases, and unique characteristics.
Microsoft Exchange GAL
Microsoft Exchange is perhaps the most commonly referenced platform when discussing GALs.
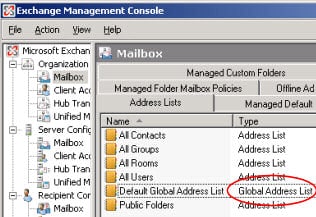
Here, the GAL is a directory service that contains the email addresses and other contact information for all users within an Exchange organization.
- Features: Integration with Microsoft Outlook, support for distribution lists, and customization options are some of the features that set it apart.
- Use-Cases: Ideal for organizations heavily invested in the Microsoft ecosystem, including those using Office 365.
- Unique Characteristics: Seamless integration with Active Directory, support for complex queries, and high-level customization.
LDAP-based GALs
The Lightweight Directory Access Protocol (LDAP) provides another avenue for implementing a GAL. An LDAP-based GAL is generally more flexible and can be integrated into a variety of environments.
- Features: Advanced querying capabilities, support for multiple object types, and a standardized protocol for directory services.
- Use-Cases: Suited for heterogeneous environments where multiple operating systems and email platforms are in use.
- Unique Characteristics: Ability to interface with a multitude of services beyond email, such as VoIP systems and third-party applications.
Cloud-based GALs
With the advent of cloud computing, GALs have also moved to the cloud, offering increased accessibility and reduced maintenance overhead.
- Features: Remote accessibility, automated updates, and robust disaster recovery options.
- Use-Cases: Ideal for organizations that have adopted a cloud-first approach and have a mobile, globally distributed workforce.
- Unique Characteristics: Typically offered as a service, cloud-based GALs often come with built-in features like AI-driven analytics and advanced security protocols.
Understanding the types of GALs available can help organizations make informed decisions that align with their specific needs and technological landscapes. Each type offers its own set of advantages and limitations, requiring a thoughtful approach to selection and implementation.
3. Configurations and Settings
Configuring GAL in Microsoft Exchange
In Microsoft Exchange environments, setting up the Global Address List usually starts with the Exchange Admin Center (EAC) or Exchange Management Shell for more advanced configurations. Admins can specify which object types to include, such as users, contacts, and groups, as well as which attributes (like job title or department) to display. Additionally, it’s possible to create multiple GALs based on organizational needs, each filtered by specific criteria.
- Navigate to EAC: Access the Exchange Admin Center and go to “Recipient > Global Address Lists.”
- Create or Edit GAL: You can create a new GAL or modify an existing one. Define the rules and conditions that should be applied.
- Attribute Mapping: If needed, custom attributes can be mapped to be visible when a user accesses the GAL through Outlook.
- Permissions: Ensure the appropriate permissions are set so that only authorized personnel can make changes to the GAL.
- Propagation: Note that changes may take some time to propagate throughout the network, depending on its size and complexity.
Customizing LDAP-based GALs
LDAP-based Global Address Lists offer a bit more flexibility and can be highly customized to suit an organization’s needs. By leveraging LDAP queries, you can fine-tune what information is pulled into the GAL.
- LDAP Server Access: Connect to your LDAP server using admin credentials.
- Query Configuration: Write an LDAP query that specifies which entries and attributes to include in your GAL.
- Attribute Customization: Just like in Exchange, you can define custom attributes to appear in the GAL.
- Testing: Always test the configuration in a controlled environment before rolling it out to the entire network.
Settings in Cloud-based Solutions
Cloud-based solutions like Google Workspace and Microsoft 365 also offer GAL features, often with simplified setup due to the managed nature of these platforms.
- Access Admin Console: Log into the administrative console of your cloud-based service.
- Navigate to Directory Settings: Find the section related to user directories or GAL.
- Set Criteria: Define which users or resources should appear in the list and any applicable organizational units.
- Sync Settings: Some cloud services offer real-time sync, ensuring the GAL is always up-to-date.
4. Global Access List Interoperability
GAL with Active Directory
In many enterprise environments, the Global Address List is closely tied with Active Directory (AD). Exchange’s GAL often pulls its data from the AD schema, providing seamless integration. It’s crucial to ensure the attribute mappings are correctly configured so that information flows accurately between AD and the GAL.
GAL in Cross-platform Environments
Interoperability becomes an essential aspect when dealing with GALs in heterogeneous or cross-platform environments, which may involve different operating systems and directory services. Here, standard protocols like LDAP can act as a bridge. Tools and services that can sync or “federate” multiple GALs are also available, ensuring that users across disparate systems can find and communicate with each other efficiently.
Understanding the configurations, settings, and interoperability options for Global Address Lists—whether in Microsoft Exchange, LDAP-based setups, or cloud-based solutions—enables businesses to optimize this valuable resource for enhanced collaboration and security.
5. GAL Security Aspects
Access Controls
Access to the Global Address List should be meticulously managed to safeguard sensitive data and prevent unauthorized alterations. Most systems provide role-based access control (RBAC) settings that allow administrators to specify who can read or modify the GAL.
- Read-Only Access: Basic users typically have read-only access, ensuring they can look up contacts but not make changes to the list.
- Admin Access: Only trusted admins should have the ability to modify the GAL, adding or deleting entries as needed.
- Group-based Access: In more complex scenarios, you may configure group-based permissions, where certain departments or teams have access to specialized sub-lists within the GAL.
Encryption
Encrypting the Global Address List is critical, especially in an era when cyber threats are on the rise. Many platforms offer built-in encryption both at rest and in transit, ensuring that the GAL data is secured.
- Data at Rest: The database storing the GAL should be encrypted to protect against unauthorized data extraction.
- Data in Transit: As information is accessed or updated in the GAL, secure protocols like SSL/TLS should be used to encrypt the data during transmission.
Audit and Monitoring
Keeping an eye on who is doing what with your GAL is vital for maintaining its integrity and security.
- Activity Logging: All access and modification activities should be logged for future reference and auditing.
- Anomaly Detection: Automated systems can alert administrators about unusual access patterns or modifications, which could be indicative of a security issue.
- Regular Audits: Scheduled audits of the GAL and its associated logs should be a part of your organization’s security protocol, ensuring that only the correct individuals have access and that all activities are up to standard.
6. GAL Use Cases
Internal Communication
The most basic use of the Global Address List is for internal communication within an organization. Employees can quickly find contact details of their colleagues, enabling seamless communication through email, chat, or other internal platforms.
Collaboration Tools
Many modern collaboration tools integrate with the GAL to simplify setup and use. For example, when creating a new team in Microsoft Teams or Slack, the GAL can auto-populate potential team members, simplifying the setup process and enhancing user experience.
CRM and ERP Systems
Customer Relationship Management (CRM) and Enterprise Resource Planning (ERP) systems often integrate with an organization’s GAL. This provides a unified directory of contacts that can be accessed across different departments, ensuring everyone is working with the most up-to-date information.
By acknowledging the critical security aspects and recognizing the diverse use cases, organizations can optimize their Global Address List as a powerful tool for internal communications, collaborations, and integrated enterprise solutions.
7. Global Address List Best Practices
Regular Updates
It’s essential to keep the Global Address List up-to-date to maintain its usefulness and accuracy. Implementing a routine for regular updates ensures that all new hires are added promptly and that employees who have left the organization are removed.
- Automated Updates: Consider setting up automated processes that sync with your HR system to add or remove employees automatically.
- Notification Systems: Use notifications to remind administrators to review and update the GAL regularly.
Cleanup and Validation
An outdated or cluttered GAL can be more of a hindrance than a help. Regular cleaning and validation activities should be part of your maintenance strategy.
- Duplicate Entries: Use scripts or specialized software to identify and remove duplicate entries.
- Data Validation: Regularly validate email addresses, phone numbers, and other contact details to ensure they are current.
Security Policies
A well-defined security policy is crucial for maintaining the integrity and confidentiality of your GAL.
- User Training: Educate users on the importance of not sharing sensitive information found in the GAL.
- Access Review: Conduct periodic reviews to ensure only authorized personnel have access to the GAL, in line with the principle of least privilege.
8. Emerging Trends
Integration with IoT
The Internet of Things (IoT) brings new possibilities for GAL functionality. As more devices become “smart” and connect to corporate networks, the GAL can evolve to include device contacts, expanding its role from a human-focused list to a broader directory of networked resources.
AI-driven GAL Management
Artificial Intelligence (AI) offers intriguing options for automating and optimizing GAL management. Predictive algorithms can suggest updates, identify duplicates, or even flag potential security risks based on user behavior and access patterns.
9. Conclusion
The Global Address List is a vital resource for internal communication, collaboration tools, and integrated enterprise solutions like CRM and ERP systems. A well-managed GAL enhances organizational efficiency and contributes to a robust security posture.
Expanding Role of GAL in Modern Networking
Finally, as technology evolves, so does the role of the GAL. With advancements in AI and the rise of IoT, the GAL is set to expand beyond a simple list of human contacts. It’s becoming an intelligent, dynamic tool that plays a central role in a multifaceted networking landscape. Keeping up with these trends and applying best practices will ensure that your GAL remains a valuable asset in your organization’s toolkit.