In the digital universe where data is king, the importance of distinctly identifying each piece of information cannot be overstated. Enter the Globally Unique Identifier (GUID), a 128-bit value that offers a high degree of uniqueness, used extensively across software applications to distinguish every entity with ironclad certainty.
This article embarks on a deep dive into the world of GUIDs, unraveling their structure, generation methods, and their critical role in ensuring data integrity across disparate systems. We’ll explore the intricate probabilities that underpin their uniqueness and the various standards that govern their format and use.
Table of Contents:
- What is a GUID?
- The Anatomy of a GUID
- Generating GUIDs
- GUID Standards and Formats
- GUIDs in Practice
- Collisions and Uniqueness
- Infographic
- References

1. What is a GUID?
A Globally Unique Identifier (GUID) is an identifier designed with a formidable 128-bit cryptographic architecture, ensuring that each generated GUID remains distinctive across all systems and points in time. It’s a cornerstone in the world of computing, widely utilized for various identification purposes — from software components to database keys, ensuring that every item remains unambiguously identifiable.
The inception of a GUID is based on algorithms that leverage both spatial and temporal dimensions, further reinforcing its uniqueness. The spatial aspect typically involves the hardware address of the machine generating the GUID, while the temporal component is often derived from the system clock. This pairing effectively mitigates the risk of duplication, even when generated independently by numerous systems around the globe.
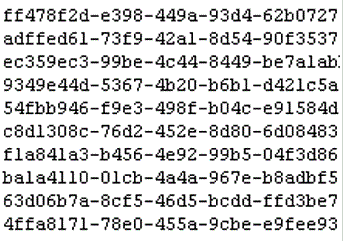
A GUID is composed of 32 hexadecimal digits, displayed in five groups separated by hyphens, in the form 8-4-4-4-12. This format is not only human-readable but also encoded with specific information like version and variant, which outline the GUID’s generation strategy and layout, respectively.
The design of GUIDs is such that they are “virtually guaranteed” to be unique. This guarantee comes from the astronomical number of possible GUIDs — over 3.4×10383.4×1038 — and the specific mechanisms used to generate them. With such an immense range of unique combinations, the probability of generating a duplicate is infinitesimally small, making GUIDs an industry standard for ensuring data distinction without the need for a centralized registry.
2. The Anatomy of a GUID
Breakdown of the 128-bit Structure
A GUID is constructed from a series of binary digits — specifically, 128 of them. To make GUIDs more interpretable for human use, these bits are expressed in hexadecimal (base-16) notation. This results in a string format that contains 32 hexadecimal digits. To further aid readability, these digits are divided into five groups: 8-4-4-4-12, separated by hyphens, which correspond to four fields with distinct purposes:
- Time_low: The first group of 8 hexadecimal digits represents the low field of the timestamp.
- Time_mid: The following group of 4 hex digits corresponds to the middle field of the timestamp.
- Time_hi_and_version: The third group contains the high field of the timestamp and the version number of the GUID.
- Clock_seq_and_reserved: The fourth group houses the clock sequence and the variant.
- Node: The final group consists of 12 hexadecimal digits that represent the node ID which is often the MAC address of the machine generating the GUID.
Variant and Version Fields Explained
The variant field determines the layout of the GUID and is critical for ensuring that GUIDs generated by different specifications are distinguishable from one another. It consists of several bits at the beginning of the clock_seq field. The most common variant in use today is specified in RFC 4122 (1), which defines the layout for Leach-Salz GUIDs.
The version field is part of the time_hi_and_version group of digits and signifies the algorithm used to generate the GUID. There are five versions defined in RFC 4122:
- Version 1: Time-based version
- Version 2: DCE security version, with embedded POSIX UID/GID
- Version 3: Name-based version using MD5 hashing
- Version 4: Randomly or pseudo-randomly generated
- Version 5: Name-based version using SHA-1 hashing
The version is indicated by the first few bits of the time_hi_and_version group, allowing software to interpret the GUID structure correctly.
3. Generating GUIDs
3.1 Algorithms and Methods
GUIDs are generated through various algorithms, each corresponding to a different version as specified by the version field:
- Version 1: Combines the MAC address of the generating device with the current time and a sequence number to prevent duplicates from the same source in the same clock cycle.
- Version 2: Similar to Version 1 but includes additional information for POSIX systems.
- Version 3 and Version 5: Use hashing (MD5 or SHA-1, respectively) of a namespace identifier and a name.
- Version 4: Uses random or pseudo-random numbers.
A complete example of a Version 1 GUID might look like this: 550e8400-e29b-11d4-a716-446655440000
Here, the first three groups represent the timestamp, the fourth group includes the version and clock sequence, and the last group is a spatial node ID.
3.2 Time-based vs. Random-based GUIDs
- Time-based GUIDs (Version 1): These rely on the current time, a clock sequence, and the machine’s MAC address to generate a unique identifier. The timestamp ensures uniqueness across time, the MAC address provides uniqueness across space, and the clock sequence covers the edge case of two GUIDs being generated at the same moment on the same machine.
- Random-based GUIDs (Version 4): These forsake the time and MAC address components, instead utilizing random numbers to fill the 128 bits. This method does not require a unique node ID (like a MAC address) and does not reveal the time at which the GUID was generated, offering a higher degree of privacy.
Both methods are designed to minimize the chances of GUID duplication, but they serve different needs based on the importance of the factors like privacy, sequence, and the availability of a unique node identifier.
3.3 Coding example (Python)
Below is a simple Python function that generates a Version 1 GUID. This function relies on the uuid module available in Python’s standard library, which can generate UUIDs including those based on the host ID (MAC address) and the current time.
import uuid
def generate_time_based_guid():
# Generate a UUID based on the host ID (MAC address) and current time
guid = uuid.uuid1()
return str(guid)
# Example usage:
if __name__ == "__main__":
new_guid = generate_time_based_guid()
print(f"Generated GUID: {new_guid}")
When you run this function, it will output a GUID that is generated using the Version 1 specification, which includes the current time and the machine’s MAC address as part of the GUID. Each call to uuid.uuid1() will produce a new GUID that is unique to the host and time at which it was generated.
4. GUID Standards and Formats
RFC 4122 and Other Relevant Specifications
The primary standard governing the structure and interpretation of GUIDs, also known as UUIDs (Universally Unique Identifiers), is RFC 4122 (1). This document lays out the formal definition of the 128-bit identifier, the method of generation, and how the bits are interpreted. It specifies five versions of GUIDs, each designed for specific scenarios and methods of generation. Additionally, there are other standards and specifications that reference or extend RFC 4122 for specific use cases, such as:
- Microsoft GUID: A version of UUID used in Microsoft Windows platforms, which is often represented as a 32-character hexadecimal string enclosed in curly braces.
- URN Namespace: Defined in RFC 2141 (4), it provides a way to express UUIDs as Uniform Resource Names, further enhancing their global uniqueness and usability across the internet.
Representation and Syntax Variations
GUIDs are typically represented in hexadecimal digits, displayed in a 5-group format separated by hyphens, such as 123e4567-e89b-12d3-a456-426614174000. However, there are variations in this representation, including:
- No hyphens: A continuous string of 32 hexadecimal characters.
- Braces: Enclosed in curly braces
{}often used in programming contexts, especially within the Microsoft ecosystem. - URN format: A prefix of
urn:uuid:is added to the GUID when expressed as a URN.
5. GUIDs in Practice
Common Use Cases in Software Development
GUIDs have a multitude of applications in software development due to their uniqueness. They are commonly used for:
- Identifying objects and entities: In object-oriented programming, GUIDs can serve as unique object identifiers.
- Session tracking: GUIDs can track user sessions in web applications.
- Distributed systems: They ensure unique identifiers across different machines without direct communication.
Database and Network Applications
In databases, GUIDs are often used as primary keys for records, ensuring that each entry can be uniquely identified without clashes. In network applications, GUIDs can identify networked devices and services, facilitating communication in large and complex systems.
6. Collisions and Uniqueness
Probability and the Myth of GUID Collisions
While theoretically possible, the probability of a GUID collision is exceedingly low. For a Version 4 GUID, the chances are about 1 in 2^122 (or roughly 5.3x10^36), making a collision extremely unlikely. For Version 1 GUIDs, which include timestamp and MAC address, the probability is even lower.
Ensuring Uniqueness Across Systems
The uniqueness of GUIDs across systems is ensured by the combination of time, unique node identifiers (like MAC addresses), and random or pseudo-random number generation. This multi-faceted approach effectively eliminates the practical likelihood of duplication.
7. Infographics

8. References
- Leach, P., Mealling, M., & Salz, R. (2005). A Universally Unique IDentifier (UUID) URN Namespace (RFC 4122). Internet Engineering Task Force (IETF).
- The Open Group. (1997). DCE 1.1: Remote Procedure Call (document number C706). The Open Group.
- Reilly, D. & Reilly, M. (2003). Java Network Programming and Distributed Computing. Addison-Wesley Professional.
- RFC 2141 – URN Syntax

