Hashing Algorithm is a mathematical procedure that takes the information contained in files and scrambles it to create a fixed-length string of numbers and characters called a hash.
What is Hashing Algorithm?
A mathematical procedure that takes the information contained in files and scrambles it to create a fixed-length string of numbers and characters called a hash.
A good hashing algorithm has the following characteristic: if you apply a hashing algorithm to some data and then change only a few bits in the data and apply the algorithm again, the two resulting hashes will differ in almost every bit.
Hashing algorithms are used extensively in cryptography for encrypting keys or messages. Examples of popular cryptographic hashing algorithms include MD2, MD4, MD5, and SHA-1. Message Digest 5 (MD5) uses a 128-bit hash, and Secure Hash Algorithm (SHA) uses a 60-bit hash. The more bits in a hash, the greater the security of the encryption process.
Hashing is also used in some database technology for creating indexes of items in a database. Hashes of database objects are generally smaller than the objects themselves, so they can be indexed and searched more quickly. You can generate unique hashes of fixed length for each database record, creating a hash table that you can use for quick searches for records.
Secure Hash Algorithms
The Secure Hash Algorithms are a family of cryptographic hash functions published by the National Institute of Standards and Technology (NIST) as a U.S. Federal Information Processing Standard (FIPS), including:
- SHA-0: A retronym applied to the original version of the 160-bit hash function published in 1993 under the name “SHA”. It was withdrawn shortly after publication due to an undisclosed “significant flaw” and replaced by the slightly revised version SHA-1.
- SHA-1: A 160-bit hash function which resembles the earlier MD5 algorithm. This was designed by the National Security Agency (NSA) to be part of the Digital Signature Algorithm. Cryptographic weaknesses were discovered in SHA-1, and the standard was no longer approved for most cryptographic uses after 2010.
- SHA-2: A family of two similar hash functions, with different block sizes, known as SHA-256 and SHA-512. They differ in the word size; SHA-256 uses 32-bit words where SHA-512 uses 64-bit words. There are also truncated versions of each standard, known as SHA-224, SHA-384, SHA-512/224 and SHA-512/256. These were also designed by the NSA.
- SHA-3: A hash function formerly called Keccak, chosen in 2012 after a public competition among non-NSA designers. It supports the same hash lengths as SHA-2, and its internal structure differs significantly from the rest of the SHA family.
One iteration within the SHA-1 compression function
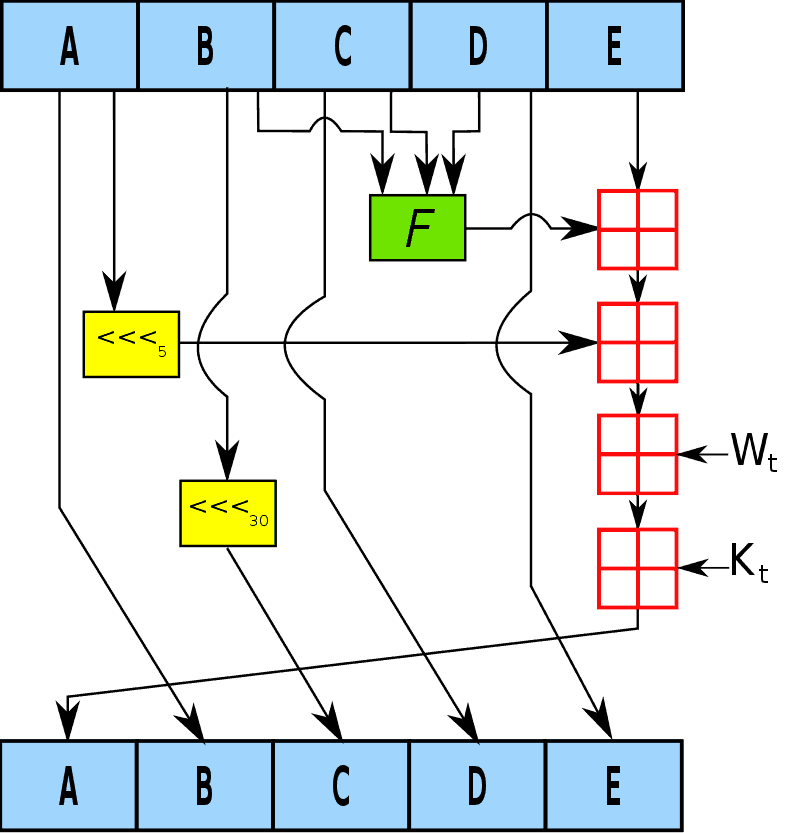
A, B, C, D and E are 32-bit words of the state; F is a nonlinear function that varies; <<<n denotes a left bit rotation by n places; n varies for each operation; Wt is the expanded message word of round t; Kt is the round constant of round t;
For more information about this topic check the Secure Hash Standard (SHS) FIPS PUB 180-4 – FEDERAL INFORMATION PROCESSING STANDARDS PUBLICATION.