In an era where the seamless flow of information is vital to both businesses and individuals, understanding how to effectively manage directory information is crucial. Lightweight Directory Access Protocol, or LDAP, stands as a cornerstone in this regard. In this article, we will unpack what LDAP is, delve into its inner workings, and explore its multitude of applications. We will also touch upon best practices and security measures you should consider when working with LDAP. Whether you’re a seasoned IT professional or a curious enthusiast, this comprehensive guide aims to enhance your understanding of this important protocol.
In this article:
- What is LDAP (Lightweight Directory Access Protocol)?
- How it Works
- LDAP Commands
- Applications and Use Cases
- Best Practices and Security Measures
- Conclusion
1. What is LDAP (Lightweight Directory Access Protocol)?
LDAP stands for Lightweight Directory Access Protocol and is an Internet protocol for accessing and updating information in an X.500-compliant directory. Users who run Lightweight Directory Access Protocol (LDAP) clients can connect to an X.500 directory service and add, delete, modify, or search for information if they have the appropriate access rights to the directory.
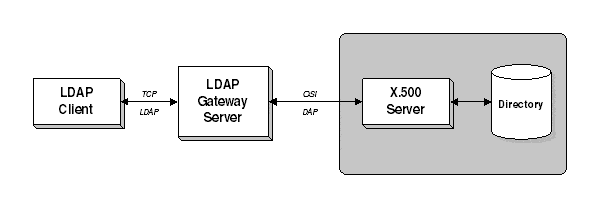
For example, a user can use an LDAP client to search a network directory for individuals, users, companies, or other information stored in the directory.
LDAP is designed to run over TCP/IP and can access information in both X.500-based directories and many non-X.500-based directories. The current version of LDAP is LDAPv3.
2. How it works
LDAP was designed by researchers at the University of Michigan to be an easier, more streamlined version of the standard X.500 Directory Access Protocol (DAP), which requires a full Open Systems Interconnection (OSI) protocol stack to run. LDAP consists of only 16 commands – 8 requests and 8 responses. These commands enable users to access, read, modify and delete information in the directory if they have the appropriate permissions. Objects are referenced using their distinguished names, as in an X.500-based directory.
A directory that is designed specifically for LDAP clients is called an LDAP directory, but this is essentially the same as the X.500 directory structure. An LDAP directory is a distributed directory; portions of the directory can be stored on different directory servers in the network. These directory servers periodically synchronize with each other to keep their information up to date. The root of an LDAP directory branches into countries, then organizations, then organizational units (departments, sections, and so on), and finally into leaf objects, which can include people, servers, printers, and other network objects.
Microsoft Exchange Server stores its directory information in an X.500-style directory. Microsoft Outlook Express was a simple LDAP client that could be used to access personal information about recipients in an Exchange organization. (Outlook Express was discontinued on October 2005)
LDAP directory services
Directory services that are not fully X.500-compliant but can be accessed and managed using LDAP are sometimes called LDAP directory services. An example of an LDAP directory is Active Directory in Microsoft Windows server family.
Objects within an LDAP directory are identified by their distinguished names, the standard namespace for X.500 directories. Distinguished names are also sometimes referred to as the LDAP Standard Naming Convention.
An LDAP Uniform Resource Locator (URL) is another naming convention that can be used to allow LDAP clients to access objects in an LDAP directory. An LDAP URL is formed by appending the distinguished name of the directory object to the fully qualified domain name (FQDN) of the server containing the LDAP directory. For example, if Active Directory is installed on the server Server7.Microsoft.com, and the distinguished name of the object being referenced in Active Directory is:
DC=com,DC=Microsoft,OU=Users,CN=Jeff Smith
the LDAP URL for referencing this object using an LDAP client is:
LDAP://Server7.Microsoft.com/CN=Jeff
Smith/OU=Users/DC=Microsoft/DC=com
3. LDAP Commands
Request Types
- BindRequest: This is used to authenticate a client to an LDAP server. The BindRequest contains credentials like username and password or other authentication methods.
- UnbindRequest: As the name suggests, this command is used to end an LDAP session, essentially “unbinding” the client from the server. No response is expected for this operation.
- SearchRequest: This is perhaps the most commonly used LDAP command. It is used to search for specific entries in the directory based on criteria like filters and attributes.
- ModifyRequest: Allows for the modification of an existing entry in the LDAP directory. Changes can include adding, deleting, or replacing attributes.
- AddRequest: Used for creating a new entry in the LDAP directory.
- DelRequest: This command is used to delete an existing entry from the LDAP directory.
- ModifyDNRequest: This command is used for changing the Distinguished Name (DN) of an entry, essentially allowing for renaming or moving entries.
- CompareRequest: Compares an attribute to a given value in an LDAP directory entry and returns whether they match or not.
Response Types
- BindResponse: Sent by the server in response to a BindRequest to indicate the result of the authentication attempt.
- SearchResultEntry: Returned for each entry that matches the SearchRequest criteria.
- SearchResultDone: Indicates the end of search results returned for a SearchRequest.
- ModifyResponse: Sent in reply to a ModifyRequest, indicating the success or failure of the operation.
- AddResponse: Sent in reply to an AddRequest, confirming the success or failure of adding a new entry.
- DelResponse: Sent in response to a DelRequest, indicating the result of the delete operation.
- ModifyDNResponse: Sent in response to a ModifyDNRequest, reporting the outcome of the DN modification.
- CompareResponse: Sent in response to a CompareRequest, indicating whether the comparison was true or false.
4. Applications and Use Cases
LDAP, a cornerstone in the tech world, serves various purposes. Firstly, it excels in directory services. Many organizations rely on it to store user account details and access permissions. Moreover, it acts as the backbone for countless enterprise-level applications.
Additionally, LDAP is instrumental in email systems. For instance, it often stores email addresses and configurations. As a result, email clients can quickly retrieve this information, streamlining the user experience.
Intriguingly, LDAP also powers network file systems like NFS. By storing pathnames and permissions, it makes file sharing more secure and efficient. Hence, it’s crucial for network administrators.
Furthermore, LDAP plays a vital role in Single Sign-On (SSO) solutions. In this context, it maintains a centralized authentication server. Consequently, users log in once and gain access to multiple services, enhancing both security and convenience.
However, that’s not all. VoIP services, for example, leverage LDAP to manage contacts and configurations. Therefore, calls get routed more efficiently, improving the overall quality of service.
Besides, many e-commerce sites use LDAP for customer data management. This centralized approach simplifies data retrieval, speeding up transactions and making the shopping experience more enjoyable.
Similarly, academic institutions employ LDAP for managing student records. This setup ensures that data is consistently accurate and readily available, thereby aiding administrative tasks.
Lastly, cybersecurity solutions like firewalls and intrusion detection systems also benefit from LDAP’s efficient data querying, adding an extra layer of security.
In summary, LDAP is not just a directory service protocol; it’s a versatile tool that powers a multitude of applications. From email systems to network security, its range of use cases is impressively broad, making it an invaluable resource in diverse settings.
5. Best Practices and Security Measures
Navigating the landscape of LDAP calls for a mindful approach, particularly when it comes to security and efficiency. So, let’s dig in.
Access Controls: First off, implement strong access control measures to safeguard sensitive information. LDAP servers often contain critical data; therefore, restricting who can access what is a no-brainer.
Use SSL/TLS: Next, it’s pivotal to encrypt data in transit. Employ SSL/TLS for securing communications between LDAP servers and clients. This adds an essential layer of security, rendering intercepted data useless to eavesdroppers.
Regular Audits: On a similar note, carry out frequent audits. These help you monitor server performance and flag any suspicious activities.
Updated Software: Importantly, always keep your LDAP server software up-to-date. Developers regularly patch security vulnerabilities, so using an outdated version is tantamount to inviting trouble.
Attribute Security: Another recommendation is to restrict which LDAP attributes can be viewed or modified by users. The less data an unauthorized user can access, the lower the security risk.
Backup Regularly: Finally, but certainly not least, back up your LDAP data consistently. If things go south, a recent backup can be a lifesaver.
6. Conclusion
Throughout this comprehensive exploration of LDAP, we’ve navigated its fundamental principles, applications, and considerations for securing and optimizing your setup. With the ever-evolving landscape of network technologies and security threats, it’s crucial to stay ahead of the curve.
LDAP, a veteran in the space, still offers robust options for directory services and will likely continue to be a mainstay in both legacy and modern systems. Hence, understanding its best practices and security measures isn’t just beneficial—it’s essential. Armed with this knowledge, you are better positioned to leverage LDAP’s capabilities while minimizing its inherent risks.