A Network Access Server (NAS) acts as a gateway between user devices and a larger network, often facilitating access to resources like files, applications, and internet connectivity. It plays a pivotal role in managing and authenticating user access, essentially serving as a network’s first line of defense and control.
In this article:
- What is a Network Access Server?
- NAS in Network Architecture
- NAS Protocols and Standards
- Security Considerations
- Configuring a Network Access Server for Remote Connections
- Conclusion
- References

1. What is a Network Access Server?
A Network Access Server (NAS) is a specialized computer server that serves as an access gateway for users connecting to a network. The NAS authenticates users, manages network sessions, and directs traffic, often acting as a bridge between user devices and broader network resources like databases, files, or internet access.
Functional Components
- Authentication Server: Validates user credentials before granting network access.
- Session Management: Maintains, tracks, and terminates user sessions.
- Traffic Routing: Directs user requests to appropriate network resources.
- Access Control Lists (ACLs): Specifies permissions for users to access certain network resources. See more
Types of NAS Devices
- Enterprise NAS: Designed for large organizations, featuring robust capabilities and scalability.
- Small Business NAS: Affordable and easy to manage, suitable for SMEs.
- Consumer NAS: Tailored for home use, often featuring user-friendly interfaces and basic features.
2. NAS in Network Architecture
Role in LANs and WANs
In a Local Area Network (LAN), a NAS typically controls access to internal resources, like shared files or printers. In a Wide Area Network (WAN), the NAS often acts as a gateway to the internet, handling external communications.
Positioning within the OSI Model
The NAS operates primarily at the Data Link and Network layers (Layers 2 and 3) of the OSI Model. It can also implement functionalities at the Transport and Application layers (Layers 4 and 7) for specific use-cases like VPN access or application-level gateways.
Typical Deployment Scenarios
- Corporate Networks: Serves as an access control point for both wired and wireless connections, often integrated with other security solutions like firewalls or intrusion detection systems.
- Internet Service Providers (ISPs): Utilized to manage large volumes of customer connections.
- Data Centers: Facilitates access to massive storage solutions and application servers.
- Home Networks: Grants family members secure access to shared files and internet connectivity.
3. NAS Protocols and Standards
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a widely used protocol for centralized authentication, authorization, and accounting (AAA) in NAS systems. It provides robust security measures and is compatible with various network devices.
TACACS+
Terminal Access Controller Access-Control System Plus (TACACS+) is another AAA protocol, commonly used in larger networks. Unlike RADIUS, which combines authentication and authorization, TACACS+ separates these processes, offering more flexibility.
LDAP
Lightweight Directory Access Protocol (LDAP) is often used for querying and modifying directory services. In a NAS context, it’s used for centralized user management, allowing for seamless authentication and authorization across a network.
Proprietary Protocols
Some NAS manufacturers develop their proprietary protocols for authentication and session management. These are usually designed to work exclusively with devices from the same manufacturer, offering unique features but potentially limiting interoperability.
4. Security Considerations
Authentication Mechanisms
Given that a primary function of a Network Access Server is to provide remote access, robust authentication mechanisms are critical. Methods such as multi-factor authentication (MFA) or token-based authentication enhance security by providing layers of verification.
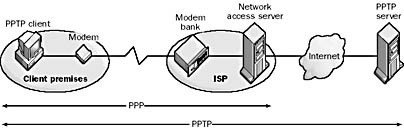
Encryption
Data transmitted between a client and a Network Access Server should always be encrypted. Protocols like RADIUS, for instance, ensure that user passwords during authentication are encrypted, but using additional encryption layers, like VPN tunnels, can enhance security further.
Firewall and IDS/IPS Integration
NAS devices should always be shielded behind firewalls to prevent unauthorized access attempts. Furthermore, integration with Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can monitor and block any malicious activities or access attempts, ensuring a secure remote access environment.
5. Configuring a Network Access Server for Remote Connections
Network Access Servers (NAS) play a pivotal role in providing remote access to network resources. Properly setting up and configuring these servers is crucial to ensure secure, reliable, and efficient remote connections. This chapter provides a comprehensive guide on configuring a NAS for optimal remote connections.
1. Determine the Server’s Role
Before anything, define the primary function of your NAS:
- Dial-up Access: For older infrastructures still using telephony systems.
- VPN Gateway: For businesses that need to offer secure remote access to their local networks over the internet.
- Wireless Access Control: For managing connections in a wireless network environment.
2. Hardware Considerations
Ensure the server has adequate hardware to handle the anticipated number of concurrent connections. This includes:
- Sufficient RAM: To manage multiple concurrent sessions.
- Powerful CPU: Especially if complex encryption methods are being used.
- Redundant Power Supplies: To maintain uptime in case one fails.
- Adequate Network Interfaces: To manage traffic without bottlenecks.
3. Integrating with Authentication Mechanisms
Choose an authentication protocol that aligns with your organization’s security policies:
- RADIUS: A widely-used protocol, especially suitable for larger organizations due to its scalability.
- TACACS+: Offers a finer granularity of access control.
- LDAP: Useful for organizations that already have an LDAP directory in place.
Integrate the NAS with the chosen authentication system and ensure encrypted communication between them.
4. Configuring Connection Policies
Define rules for:
- Access Hours: Specify when users can connect.
- Connection Duration: Limit how long a user can stay connected.
- Bandwidth Restrictions: Allocate bandwidth based on user roles or departments.
5. Encryption and Security Protocols
For secure connections, especially over the internet:
- VPN Protocols: Such as PPTP, L2TP, or IPsec.
- Data Encryption: Implement strong encryption standards to protect data during transit.
6. Monitoring and Logging
Set up monitoring tools to track:
- Active Connections: Know who is connected and for how long.
- Failed Login Attempts: A sudden spike could indicate a brute-force attack.
- Bandwidth Usage: Ensure fair usage and avoid network congestion.
Logging is essential not just for security but also for auditing and compliance. Regularly review and archive logs.
7. Regular Maintenance and Updates
Regularly update the NAS software to patch vulnerabilities. Also, periodically review and update configuration settings to adapt to changing network conditions and user requirements.
8. Backup Configurations
Always keep a backup of your NAS configurations. In case of any failures or necessary rollbacks, having a saved configuration can save significant time and effort.
10. Conclusion
The role of Network Access Servers (NAS) in the modern digital landscape cannot be overstated. As the bridge between users and the networks they aim to access, NAS devices are the sentinels and gatekeepers that ensure seamless, secure, and efficient remote connections. As we’ve traversed through this comprehensive guide, we’ve delved into the intricate components, configurations, protocols, and security considerations pivotal to a NAS.
Given the increasing trend towards remote work, global collaboration, and the need for on-the-go access to resources, the importance of NAS systems will only continue to grow. It’s no longer just about providing access—it’s about ensuring that access is secure, efficient, and in line with organizational policies and global standards.
For students and professionals in computer and network engineering, understanding the nuances of Network Access Servers is not just beneficial—it’s essential. As the digital world becomes more interconnected, the demand for experts who can design, configure, and maintain these servers will rise. Armed with the knowledge from this article, you are well on your way to becoming one of those experts.
In the age of cyber threats and an ever-evolving technological landscape, the NAS stands firm as a beacon of connectivity and security. The future will undoubtedly bring new challenges, but with a solid foundation in the principles and practices surrounding Network Access Servers, we are well-prepared to meet them head-on.