In the hidden backstage of a Windows-operated computer, lies a marvel of software engineering that serves as the backbone of data organization and management – the NTFS File System. A successor to the FAT (File Allocation Table) system, the New Technology File System (NTFS) embodies a perfect blend of reliability, performance, and security. It stands as an eloquent testament to the complexity and sophistication that underpin modern computing, transforming the abstract space of the disk into a structured, navigable landscape of files and directories.
In this article:
- What is the NTFS File System?
- Architecture and Structure of NTFS
- NTFS vs. FAT: A Comparative Analysis
- Security Features in NTFS
The elegance of NTFS transcends mere data storage. Its design harbors a wealth of advanced features like journaling, encryption, and access control, meticulously orchestrated to cater to the multifaceted needs of modern users. This article takes a compelling journey into the inner workings of the NTFS File System, unraveling its architectural brilliance, its role in the Windows ecosystem, and its continuing evolution. Whether a tech enthusiast, an IT professional, or an inquisitive user, the exploration of NTFS promises to be an intellectual adventure filled with insights and discoveries.
NTFS includes security features for data access control and ownership privileges that make it suitable for file servers, Web servers, and application servers in the corporate networking environment.
What is the NTFS File System?
The NTFS File System, or New Technology File System, is a proprietary file system developed by Microsoft. First introduced with Windows NT 3.1 in 1993, it has since become the default file system for Windows operating systems. Unlike its predecessors in the FAT family, NTFS brought along a slew of innovations and enhancements, providing a robust platform for modern computing needs.
The central purpose of NTFS is to organize and manage data on storage devices like hard drives and SSDs. It achieves this through a hierarchical structure that mirrors a tree, comprising files, folders, and various metadata attributes. But NTFS doesn’t stop at mere organization; it weaves into its fabric advanced features like journaling, which ensures data integrity, encryption for security, disk quotas for managing user space, and intricate permission systems to control access. The result is a file system that offers both flexibility and control, supporting everything from personal computing to complex enterprise-level operations.
Architecture and Structure of NTFS
The NTFS (New Technology File System) is not just a method of storing files on a disk, but a complex structure with multiple components interlocking seamlessly to offer a wide array of functions beyond mere file storage. The architecture of NTFS is an intricate blend of technical prowess and design intelligence, revealing layers of sophistication as one delves deeper into its structure. This chapter explores the architecture and structure of NTFS, unwrapping its internal components and layout, and examining the innovative mechanisms that make it a robust and versatile file system.
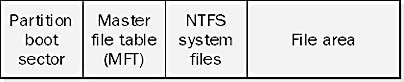
1. Master File Table (MFT)
The MFT is the heart of NTFS, a crucial database containing entries for every file and directory on an NTFS volume. Each entry, known as an MFT record, holds information about the file or directory’s attributes, such as its name, timestamp, and data content or pointers to its location. The MFT itself is stored as a file and has a backup copy within the volume.
a. Attributes in MFT Records
- Standard Information: Basic information like timestamps and permissions.
- File Name: Human-readable name of the file or directory.
- Data Attribute: The actual content of the file, or pointers if the data is large.
- Index Root and Index Allocation: Used for directories to reference other files.
2. Clusters and Sectors
A cluster is the smallest logical unit of disk space that can be allocated to hold a file. Clusters are grouped into sectors, the smallest physical units on the disk. This alignment facilitates efficient storage and retrieval, minimizing wastage.
3. Journaling: NTFS Log File
NTFS employs journaling through a system file known as the NTFS Log File. It records all transactions that affect the volume’s structure. In the event of a failure, this log enables the system to repair itself without losing data integrity.
4. File System Metadata
Metadata files store information about the file system itself, not about user data. They include the MFT, volume information, cluster allocation, and security descriptors.
5. Security Descriptors and Access Control
NTFS uses a comprehensive security model, defining permissions at the file and directory level. Security descriptors include information like ownership, permissions, and auditing settings.
6. Alternate Data Streams (ADS)
NTFS allows files to have multiple streams of data. While one stream stores the primary content, additional streams can hold metadata or other information without altering the main file.
7. Volume and Disk Management
The NTFS volume includes a Boot Sector, Volume Descriptor, and Bitmap, providing essential information for the operating system to recognize and manage the disk.
8. Sparse Files and Compression
NTFS supports sparse files, allowing efficient storage of files with large empty spaces. It also offers native compression to save space.
9. Symbolic Links and Junctions
NTFS provides mechanisms for creating symbolic links and junctions, facilitating flexible file referencing across the system.
The architecture of NTFS is a harmonious composition of various components, each playing its specific role, yet interconnected in an intricate manner. It’s a system that goes far beyond mere data organization, embedding features that encompass security, integrity, efficiency, and flexibility. From the vital MFT to the utilization of modern concepts like ADS, journaling, and symbolic links, NTFS represents a paradigm of file system design that continues to evolve and inspire. The detailed exploration of its structure not only provides an understanding of its functionality but also a profound appreciation for the ingenuity that shapes our digital world.
NTFS vs. FAT: A Comparative Analysis
The evolution of file systems is emblematic of the broader progression of digital technology, reflecting changes in hardware capabilities, software complexities, and user demands. Within the Windows ecosystem, this evolutionary path is most vividly illustrated by the shift from the File Allocation Table (FAT) system to the New Technology File System (NTFS). This transition wasn’t merely incremental but represented a paradigm shift in how data was managed and interacted with. In this chapter, we delve into a comparative analysis of NTFS and FAT, dissecting their architectures, features, performance characteristics, and utility across various contexts.
1. Architectural Overview
NTFS
NTFS, introduced with Windows NT 3.1, is a journaling file system that offers complex features like security descriptors, file encryption, disk quotas, and symbolic links. It’s built around the Master File Table (MFT), which stores metadata for all files and directories.
FAT
FAT, in its variations (FAT12, FAT16, FAT32), is a simpler file system. It uses a table to manage files, associating each file with a chain of clusters. Simplicity is its hallmark, but this also limits its capabilities in comparison to NTFS.
2. File Management and Organization
NTFS
- MFT Records: Enables detailed metadata and attribute storage.
- Hard Links and Junctions: Supports complex file referencing.
- Sparse Files: Efficient handling of large files with empty spaces.
FAT
- Cluster Chains: Simple and linear file management.
- No Sparse File Support: Less efficient for certain file types.
- Limited Metadata: Less information stored about files.
3. Security and Permissions
NTFS
- Granular Permissions: Detailed control over file access.
- Encryption Support: Native encryption capabilities.
- Auditing and Ownership: Tracking and accountability features.
FAT
- No Native Security: Lacks granular permissions and encryption.
- Minimal Protection: Essentially unprotected in terms of access control.
4. Performance and Reliability
NTFS
- Journaling: Protects integrity through transaction logging.
- Compression: Supports native file and disk compression.
- Scalability: Handles large volumes and files efficiently.
FAT
- No Journaling: Less robust against failures.
- Size Limitations: Struggles with very large files and volumes.
- Less Efficient: Generally slower and less resourceful with space.
5. Compatibility and Use Cases
NTFS
- Modern Windows Systems: Default for Windows NT and later.
- Limited Cross-Platform: Some support in non-Windows systems, but less universal.
FAT
- Broad Compatibility: Supported across many platforms and devices.
- Ideal for Removable Media: Commonly used for USB drives, SD cards, etc.
The contrast between NTFS and FAT is a microcosm of the broader technological evolution that characterizes the digital age. While FAT’s simplicity and compatibility made it a stalwart in the early days of computing, NTFS emerged as a response to the increasingly sophisticated needs of modern computing.
NTFS brought not only greater efficiency and reliability but also introduced a range of features that transformed the file system from a mere storage mechanism into a versatile tool for managing, securing, and leveraging data. It’s emblematic of a holistic approach to design, where considerations extend beyond primary functionality to encompass the myriad ways in which users and systems interact with data.
Yet, FAT’s enduring legacy is a testament to the importance of context, serving specific use cases like removable media, where its simplicity is an advantage. The juxtaposition of NTFS and FAT is thus not merely a comparison of two technologies but an illustration of how design choices reflect and shape the broader technological landscape and user experience.
Security Features in NTFS
The security of information is paramount in our interconnected and digitalized world. With a growing array of threats, security isn’t simply an add-on but a foundational element that is integrated into the very core of systems and technologies. The New Technology File System (NTFS), employed by Windows operating systems, embodies this integrated approach to security, offering an array of features that govern access, protect data, and ensure the integrity of information. This chapter delves into the security features in NTFS, exploring how they work, why they are important, and how they fit into the broader landscape of information security.
1. Access Control Lists (ACLs)
ACLs are at the heart of NTFS’s security model, providing a robust mechanism to specify who can access files and directories and what they can do with them.
- Permissions: NTFS allows for fine-grained permissions at the file and directory levels, including Read, Write, Execute, and Delete.
- Inheritance: ACLs can be inherited from parent directories, ensuring consistent security policies.
- Explicit Deny: Specific deny rules can be applied to override inherited permissions, offering precise control.
2. Encryption: Encrypting File System (EFS)
EFS is a feature in NTFS that enables transparent encryption and decryption of files, safeguarding sensitive data.
- User-Based Encryption: Files are encrypted with a user-specific key, ensuring that only the authorized user can access them.
- Recovery Agents: Designated recovery agents can access encrypted files if necessary, ensuring business continuity.
3. Auditing
NTFS offers extensive auditing capabilities, allowing administrators to track who has accessed files, what they have done, and when.
- Configurable Auditing: Auditing can be tailored to specific needs, such as tracking access to sensitive files or monitoring changes.
- Integration with Event Viewer: Auditing logs are integrated with the Windows Event Viewer, allowing for comprehensive monitoring and reporting.
4. Disk Quotas
Disk quotas enable administrators to control how much disk space users can consume, ensuring fair usage and preventing abuse.
- Per-User Quotas: Administrators can set quotas for individual users or groups.
- Warnings and Limits: Users can be warned as they approach their quota and restricted if they exceed it.
5. File and Folder Attributes
NTFS supports various attributes that enhance security, such as making files read-only, hidden, or system files.
- Immutable Files: By setting files as read-only, they can be protected from accidental or malicious changes.
- Hidden Files: Sensitive files can be hidden, reducing the risk of unauthorized access.
The security features in NTFS are emblematic of a broader trend in technology design, where security is integrated into the very fabric of systems and processes. By offering granular access control, robust encryption, comprehensive auditing, and other features, NTFS ensures that security isn’t merely a layer applied to information but a core part of how information is managed and interacted with.
In a world where information is a valuable commodity, and threats are ever-evolving, the security features in NTFS offer a dynamic and flexible toolkit to safeguard data. From individual users safeguarding personal files to enterprises protecting mission-critical data, NTFS’s security features play a vital role in the contemporary digital landscape. They illustrate a thoughtful and holistic approach to design, where security is not an afterthought but a central consideration, reflecting the realities and demands of our interconnected world.