In the NTFS file system, the concept of ‘Owner’ plays a pivotal role in managing file permissions and security. Essentially, the Owner is the user or entity that wields ultimate control over a file’s permissions, typically being the file’s creator. By default, the Owner has the authority to modify the object’s discretionary access control list (DACL), empowering them to grant or restrict user and group permissions for various objects.
This article delves into the intricacies of file ownership in NTFS, highlighting its impact on file security and access control. We will explore several key aspects: the fundamentals of NTFS, the characteristics and implications of file ownership, the capabilities of administrators regarding file ownership, and the specific dynamics of ownership within Active Directory environments.
Table of Contents:
- What is NTFS?
- What is File Ownership in NTFS?
- The Power of Administrators in File Ownership
- File Ownership in the Context of Active Directory
- References
1. What is NTFS?
NTFS (New Technology File System) is the standard file system for Windows operating systems. Introduced with Windows NT, it brought significant improvements in terms of performance, reliability, and disk space utilization over its predecessors. Key features include support for large volumes, robust file security mechanisms, and advanced data recovery capabilities. Understanding NTFS is crucial for comprehending how file ownership and permissions work within a Windows environment.
2. What is File Ownership in NTFS?
In the NTFS file system, the Owner is the person ultimately responsible for the permissions assigned to a file, usually the creator of a file. By default, the owner of a file has permission to modify the object’s discretionary access control list (DACL) by granting users and groups permissions for various objects.
A file always has an owner. Ownership creates a trail of accountability for the file. The ownership of a file on an NTFS volume can be changed in two ways:
- The user who owns the file, or any user who has full control permission on the file, can grant the NTFS take ownership permission to another user, thus allowing that user to take ownership of the file by using the file’s Security property sheet. Users can be allowed to take ownership of a file they do not own, but ownership cannot be assigned to them by other users (even the original owner or an administrator).
- Members of the Administrators group can always take ownership of any file by using the Security property sheet. When an administrator takes ownership of a file, the Administrators group becomes the owner of the file, not the individual administrator.
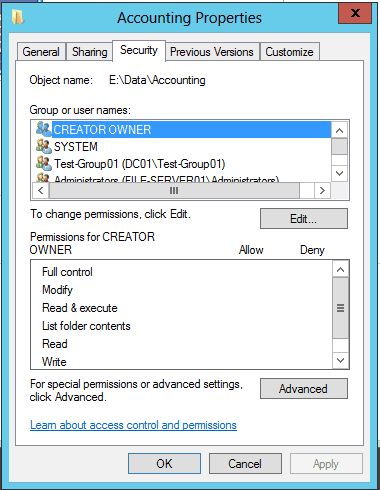
How ownership affects file access and security settings
Ownership in NTFS is intrinsically linked to file access and security settings, forming the backbone of data protection and access control within the file system. When a user becomes the owner of a file or folder, they gain the authority to set permissions that dictate how other users and groups can interact with that object. These permissions are encapsulated within the file’s Access Control List (ACL), with the Discretionary Access Control List (DACL) being a key component. The DACL comprises an ordered list of access control entries (ACEs), each specifying the access rights granted or denied to a user or group. As the owner, a user has the privilege to modify the DACL, allowing them to grant permissions like read, write, execute, or delete to others or revoke them as necessary. This level of control ensures that the owner can safeguard sensitive data, restrict access to critical files, or delegate responsibilities by granting specific permissions to other users or groups.
Furthermore, the impact of ownership on security settings is profound. In NTFS, ownership not only determines who can alter file permissions but also plays a pivotal role in auditing and accountability. When changes are made to a file or folder, the owner’s identity is often logged, creating an audit trail that can be essential for security assessments and compliance purposes. This aspect of ownership is particularly crucial in environments where data integrity and traceability are paramount. Moreover, in scenarios where a file’s security is compromised, determining the owner can be vital in resolving security breaches or policy violations. The owner’s ability to change permissions also includes setting advanced security settings such as encryption with the Encrypting File System (EFS) or implementing mandatory integrity control, which assigns integrity levels to objects, further fortifying the security framework within the NTFS file system.
3. The Power of Administrators in File Ownership
Administrators in an NTFS system wield substantial power, especially concerning file ownership. They possess the unique ability to take ownership of files and directories, regardless of who the original owner is. This authority is crucial in various scenarios, such as when a user leaves an organization and their files need to be accessed, or when files become inaccessible due to corruption or misconfigured permissions.
One key scenario where administrators might need to exercise this power is during system migrations or backups. When moving files between different systems or domains, ownership and permissions issues can arise, potentially hindering the process. Administrators can resolve these issues by taking ownership, and ensuring a smooth transition of files and data.
The process of changing file ownership involves several steps. Administrators can take ownership either through the file’s properties dialog in the Windows graphical user interface or using command-line tools like takeown or PowerShell cmdlets. After taking ownership, administrators can also assign ownership to another user or group, which is a common practice in delegation or to comply with organizational policies.
However, these changes have significant implications for file security and organizational policies. When an administrator takes ownership of a file, they can change permissions, potentially affecting data confidentiality and integrity. Organizations need to have clear policies on when and how administrators should exercise this power to prevent misuse or accidental exposure of sensitive information. Regular audits and log reviews can ensure these actions are in line with policy and necessary for operational needs.
4. File Ownership in the Context of Active Directory
Active Directory (AD) introduces additional layers of complexity and control to the concept of file ownership within NTFS. In an AD environment, file ownership extends its influence beyond local file systems to network resources and shared data. This integration plays a pivotal role in how permissions are managed and enforced across a networked environment.
In an AD setting, NTFS file ownership integrates with AD’s security principles. For instance, when a user creates a file on a network share, the file ownership can include not just the user’s account but also the groups they are a part of. This integration allows for a more nuanced and organization-wide approach to access control and permissions management.
Moreover, the role of Group Policies in AD significantly impacts file ownership norms. Group Policies can be used to enforce certain ownership and permission settings across the network. For example, a policy can be set to ensure that files created in certain network locations are owned by a specific group, thereby streamlining access control and maintaining consistency in file permissions across the organization.
Additionally, in AD environments, the concept of inheritance plays a crucial role. File and folder permissions, including ownership attributes, can be inherited from parent containers, which simplifies the management of permissions but also requires careful planning and understanding of the inheritance hierarchy to avoid unintended access grants or denials.
5. References
- “Windows Internals” by Mark Russinovich and David Solomon
- Microsoft’s NTFS Technical Reference
- RFC 3648: Web Distributed Authoring and Versioning (WebDAV) Ordering Protocol
- Microsoft’s Active Directory documentation