In a Peer-To-Peer Network, the “peers” are computer systems that are connected to each other via the Internet. Files can be shared directly between systems on the network without the need for a central server. In other words, each computer on a P2P network becomes a file server as well as a client.
Contents (this page)
- What is a Peer-to-Peer Network?
- How P2P works
- Peer-to-Peer network architecture
- Applications and examples of P2P networks
What is a Peer-to-Peer Network?
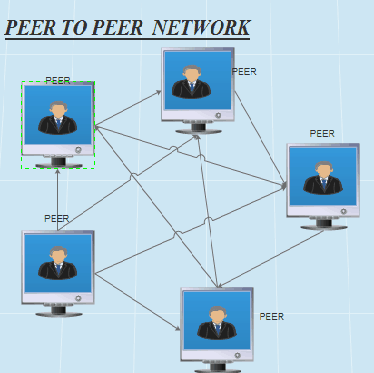
It’s a network in which the computers are managed independently of one another and have equal rights for initiating communication with each other, sharing resources, and validating users.
How It Works
A peer-to-peer network has no special server for authenticating users. Each computer manages its own security, so a separate user account might need to be created for each computer that a user needs to access. Users usually store files on their own computers and are responsible for ensuring that those files are appropriately backed up. In a peer-to-peer network, each computer typically runs both client and server software and can be used to make resources available to other users or to access shared resources on the network.
Peer-to-peer networks are simple to set up and are often ideal for small businesses that have fewer than 10 computers and that cannot afford a server-based solution. The disadvantages of peer-to-peer networks are poor security and lack of centralized file storage and backup facilities.
Peer-to-Peer network architecture
A peer-to-peer network is designed around the notion of equal peer nodes simultaneously functioning as both “clients” and “servers” to the other nodes on the network. This model of network arrangement differs from the client–server model where communication is usually to and from a central server. A typical example of a file transfer that uses the client-server model is the File Transfer Protocol (FTP) service in which the client and server programs are distinct: the clients initiate the transfer, and the servers satisfy these requests.
Peer-to-peer networks generally implement some form of virtual overlay network on top of the physical network topology, where the nodes in the overlay form a subset of the nodes in the physical network. Data is still exchanged directly over the underlying TCP/IP network, but at the application layer peers are able to communicate with each other directly, via the logical overlay links (each of which corresponds to a path through the underlying physical network). Overlays are used for indexing and peer discovery and make the P2P system independent from the physical network topology. Based on how the nodes are linked to each other within the overlay network, and how resources are indexed and located, we can classify networks as unstructured or structured (or as a hybrid between the two).
Unstructured networks
Unstructured peer-to-peer networks do not impose a particular structure on the overlay network by design, but rather are formed by nodes that randomly form connections to each other. (Gnutella, Gossip, and Kazaa are examples of unstructured P2P protocols).
Because there is no structure globally imposed upon them, unstructured networks are easy to build and allow for localized optimizations to different regions of the overlay. Also, because the role of all peers in the network is the same, unstructured networks are highly robust in the face of high rates of “churn” – that is, when large numbers of peers are frequently joining and leaving the network.

However, the primary limitations of unstructured networks also arise from this lack of structure. In particular, when a peer wants to find the desired piece of data in the network, the search query must be flooded through the network to find as many peers as possible that share the data. Flooding causes a very high amount of signaling traffic in the network, uses more CPU/memory (by requiring every peer to process all search queries), and does not ensure that search queries will always be resolved. Furthermore, since there is no correlation between a peer and the content managed by it, there is no guarantee that flooding will find a peer that has the desired data. Popular content is likely to be available at several peers and any peer searching for it is likely to find the same thing. But if a peer is looking for rare data shared by only a few other peers, then it is highly unlikely that the search will be successful.
Structured networks
In structured peer-to-peer networks, the overlay is organized into a specific topology, and the protocol ensures that any node can efficiently search the network for a file/resource, even if the resource is extremely rare.
The most common type of structured P2P networks implements a distributed hash table (DHT), in which a variant of consistent hashing is used to assign ownership of each file to a particular peer. This enables peers to search for resources on the network using a hash table: that is, (key, value) pairs are stored in the DHT, and any participating node can efficiently retrieve the value associated with a given key.

However, in order to route traffic efficiently through the network, nodes in a structured overlay must maintain lists of neighbors that satisfy specific criteria. This makes them less robust in networks with a high rate of churn (i.e. with large numbers of nodes frequently joining and leaving the network). A more recent evaluation of P2P resource discovery solutions under real workloads has pointed out several issues in DHT-based solutions such as high cost of advertising/discovering resources and static and dynamic load imbalance.
Notable distributed networks that use DHTs include Tixati, an alternative to BitTorrent’s distributed tracker, the Kad network, the Storm botnet, YaCy, and the Coral Content Distribution Network. Some prominent research projects include the Chord project, Kademlia, PAST storage utility, P-Grid, a self-organized and emerging overlay network, and CoopNet content distribution system. DHT-based networks have also been widely utilized for accomplishing efficient resource discovery for grid computing systems, as it aids in resource management and scheduling of applications.
Applications and examples of P2P networks
Content delivery
In P2P networks, clients both provide and use resources. This means that unlike client-server systems, the content-serving capacity of peer-to-peer networks can actually increase as more users begin to access the content (especially with protocols such as BitTorrent that require users to share, refer a performance measurement study). This property is one of the major advantages of using P2P networks because it makes the setup and running costs very small for the original content distributor.
File-sharing networks
Many file peer-to-peer file sharing networks, such as Gnutella, G2, and the eDonkey network popularized peer-to-peer technologies.
- Peer-to-peer content delivery networks.
- Peer-to-peer content services, e.g. caches for improved performance such as Correli Caches
- Software publication and distribution (Linux distribution, several games); via file sharing networks.
Copyright infringements
Peer-to-peer networking involves data transfer from one user to another without using an intermediate server. Companies developing P2P applications have been involved in numerous legal cases, primarily in the United States, over conflicts with copyright law. Two major cases are Grokster vs RIAA and MGM Studios, Inc. v. Grokster, Ltd.. In the last case, the Court unanimously held that defendant peer-to-peer file-sharing companies Grokster and Streamcast could be sued for inducing copyright infringement.
Multimedia
- The P2PTV and PDTP protocols.
- Some proprietary multimedia applications use a peer-to-peer network along with streaming servers to stream audio and video to their clients.
- Peercasting for multicasting streams.
- Pennsylvania State University, MIT and Simon Fraser University are carrying on a project called LionShare designed for facilitating file sharing among educational institutions globally.
- Osiris is a program that allows its users to create anonymous and autonomous web portals distributed via P2P network.
Energy trading
Companies such as Power Ledger and Bovlabs employ peer-to-peer energy trading platforms.
Bitcoin
Bitcoin and alternatives such as Ether, Nxt, and Peercoin are peer-to-peer-based digital cryptocurrencies.