Welcome to the definitive guide on Post Office Protocol version 3 (POP3), one of the core protocols that power our email systems. Whether you’re a student, an IT professional, or just a curious tech enthusiast, this article aims to be your comprehensive resource for understanding all aspects of POP3.
From its historical context to its current-day applications, from basic functionalities to its relative advantages and disadvantages, we’ve got it all covered. So, let’s deep dive into the fascinating world of POP3.
Jump to:
- What is Post Office Protocol version 3 (POP3)?
- How Does POP3 Work?
- POP3 vs IMAP vs SMTP
- Advantages and Disadvantages of POP3
- Security Concerns and Measures
- References & Further Reading
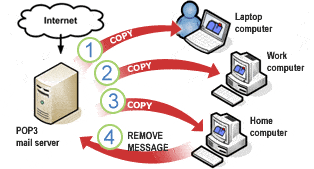
What is Post Office Protocol version 3 (POP3)?
Definition
Post Office Protocol version 3, colloquially known as POP3, is an application-layer protocol used in the world of email communication. At its core, POP3 enables email clients—think Microsoft Outlook, Apple Mail, or Thunderbird—to fetch messages from a remote SMTP email server to your local device. Operating over well-known port 110 for non-encrypted sessions and port 995 for SSL/TLS encrypted sessions, POP3 is one of the cornerstone protocols that enable email functionalities.
Historical Background
The journey of POP3 dates back to the 1980s. Imagine a time when the Internet was still in its infancy, and email was a novel concept. The first iteration of the Post Office Protocol was, let’s just say, elementary. POP3 is the third and most refined version of this protocol, standardized in 1988. It evolved to address the limitations of its predecessors, providing a more secure and efficient way to handle email data. POP3 was formalized as a standard in RFC 1939 in 1996.
Basic Functionality
So, how does POP3 do its magic? Well, the essence of POP3 lies in its model of operation: “download and delete.” When you connect your email client to a POP3 server, the server presents a list of new messages, if any. Your email client then downloads these messages and typically deletes them from the server. Voila! Your emails are now stored on your local device, accessible even when you’re offline.
Here are some of its core functionalities in a nutshell:
- Message Retrieval: The primary job of POP3. It pulls emails from the server to your local machine.
- Port Utilization: Standard POP3 uses port 110, but if you’re using POP3 over SSL (an encrypted version), you’ll be working with port 995.
- Stateless Operation: POP3 doesn’t maintain any sort of ongoing connection between the client and server. Each session is independent and generally culminates in the deletion of downloaded messages from the server.
- Authentication: Before you can grab your emails, POP3 makes sure it’s really you. Username and password are generally the keys to this digital kingdom, although more advanced security features can also be used.
By understanding these basic functionalities, you’re already ahead of the curve. POP3 may be an old dog in Internet years, but it still has some useful tricks up its sleeve. Whether you’re setting up a personal email or configuring a corporate communication system, understanding POP3 gives you the foundational knowledge to make informed decisions.
How Does POP3 Work?
SMTP provides the underlying transport mechanism for sending e-mail messages over the Internet, but it does not provide any facility for storing messages and retrieving them. SMTP hosts must be continuously connected to one another, but most users do not have a dedicated connection to the Internet.
Post Office Protocol version 3 (POP3) provides mechanisms for storing messages sent to each user and received by SMTP in a receptacle called a mailbox. A POP3 server stores messages for each user until the user connects to download and read them using a POP3 client such as Microsoft Outlook, Microsoft Outlook Express, or Microsoft Mail and News.
Session Initialization: The Handshake
The process starts when the email client initiates a TCP connection with the server. Remember, we’re talking about port 110 for non-encrypted communication and port 995 for SSL/TLS encrypted sessions. The server responds with a +OK greeting, signaling its readiness to commence the transaction. Any failure at this point usually leads to the termination of the session.
Authentication Phase: Who Are You?
Before any data exchange occurs, you have to prove your identity. This is the Authentication Phase. Typically, the USER and PASS commands are employed for sending the username and password, respectively. For those prioritizing security, alternative methods like APOP (Authenticated Post Office Protocol) may also be used, which allows for a hashed, more secure credential exchange.
Transaction Phase: Let’s Talk Business
Once authentication is successful, we enter the Transaction Phase. Here are some of the key POP3 commands:
STAT: Retrieves mailbox statistics.LIST: Lists the message numbers and sizes.RETR: Retrieves a specific message.DELE: Marks a message for deletion.NOOP: A no-operation command to keep the connection alive.QUIT: Ends the POP3 session.
Each command from the client is met with a response from the server, either confirming successful execution with +OK or indicating failure with -ERR.
Update Phase: Wrapping Up
Closing out the session is the Update Phase. Upon issuing the QUIT command, the client prompts the server to enter this phase, during which any messages marked for deletion are permanently removed from the mailbox. The server then sends a +OK response and closes the TCP connection.
Data Movement: Pull, Don’t Push
One salient feature of POP3 to remember is that it’s a ‘pull’ protocol. This means that the email client actively requests or “pulls” data from the server rather than the server “pushing” data to the client. This is a defining trait that distinguishes POP3 from some real-time ‘push’ services.
Stateless Operation: No Strings Attached
In POP3, each transaction is isolated. Unlike IMAP, which maintains session state, POP3 does not keep any information between successive sessions. This stateless nature simplifies the protocol but imposes limitations on multi-device synchronization.
By comprehending these stages and functionalities, you’re not just scratching the surface of POP3—you’re delving deep into its operational essence, equipping you with the knowledge to navigate a myriad of real-world applications and challenges.
POP3 vs IMAP vs SMTP
Understanding the realm of email protocols is incomplete without discussing the trifecta: Post Office Protocol version 3 (POP3), Internet Mail Access Protocol (IMAP), and Simple Mail Transfer Protocol (SMTP). Though all three are implicated in email functionality, their roles, characteristics, and optimal use-cases are remarkably distinct.
Core Functionalities: A Brief Overview
- POP3: Primarily designed for downloading messages from an email server to a local client, following a ‘pull’ model. Typically operates over port 110 or 995 (SSL/TLS).
- IMAP: Enables multiple devices to access the same mailbox, offering more complex functionalities like folder management and email flagging. Operates over port 143 or 993 (SSL/TLS).
- SMTP: Concerned with the delivery of emails from a client to a server or between servers. It doesn’t retrieve messages and typically operates over port 25, 587, or 465 (SSL/TLS).
POP3: The Local Hero
- Strengths:
- Offline Access: Emails are stored locally.
- Resource Efficiency: Frees up server space by deleting messages post-download.
- Limitations:
- No Multi-Device Synchronization: Messages are tied to a single device.
- Limited Server-Side Management: Lacks advanced features like folder organization.
IMAP: The Synchronized Maven
- Strengths:
- Multi-Device Sync: Access the same emails and folder structure across various devices.
- Server-Side Organization: Extensive options for categorizing and managing emails.
- Limitations:
- Requires Continuous Internet Access: To view new messages and folders.
- Consumes More Server Resources: Messages and folders are stored server-side.
SMTP: The Delivery Guru
- Strengths:
- Efficient Routing: Utilizes Domain Name System (DNS) for optimal routing.
- Supports Batch Operations: Capable of sending multiple emails in a single session.
- Limitations:
- Unidirectional: Solely for sending emails, not for retrieval.
- No Native Encryption: Security features often require additional configurations.
The Choice Matrix: When to Use What?
- POP3: Ideal for single-device setups, with limited server resources and a need for offline email access.
- IMAP: Best suited for users who need to access their emails from multiple devices with a consistent view.
- SMTP: Always used in conjunction with either POP3 or IMAP to handle the sending of emails. Not a replacement but a complement.
Understanding the core functionalities and distinctions between POP3, IMAP, and SMTP is essential for anyone dealing with network communications and email configurations. Each protocol shines in its unique set of scenarios, and knowing when to employ each can make a significant difference in your email experience.
Advantages and Disadvantages of POP3
Navigating the labyrinth of email protocols can be daunting, especially when trying to determine which one best suits your needs. Among the frontrunners is Post Office Protocol version 3 (POP3), a protocol with its own set of unique advantages and disadvantages. Let’s delve into both sides of the coin to provide you with a holistic perspective.
Advantages of Using POP3
- Offline Access: One of POP3’s hallmark features is its ability to download email messages to the client’s local storage, facilitating offline access to your email repository.
- Resource Efficiency: By storing emails locally and typically removing them from the server post-download, POP3 conserves server resources and helps avoid mailbox quotas.
- Security: While the basic authentication methods can be simplistic, secure connections via SSL/TLS are supported for added security.
- Simplicity and Speed: With its straightforward command set and session steps, POP3 can be faster and less complex than its IMAP counterpart, especially when dealing with large mailboxes.
- Bandwidth Efficiency: Given that emails are downloaded and stored locally, successive checks for new email consume less bandwidth than protocols that keep messages on the server.
Disadvantages of Using POP3
- Lack of Multi-Device Synchronization: Unlike IMAP, POP3 does not natively support multi-device synchronization. If you read an email on one device, it won’t be marked as read on others.
- Limited Server-Side Features: Advanced functionalities like folder management, flagging, and categorizing emails are either rudimentary or nonexistent in POP3.
- Risk of Data Loss: Since emails are downloaded to local storage, hardware failure can result in data loss unless a backup strategy is employed.
- Stateless Nature: POP3 sessions are stateless, meaning that any actions like message deletion are irreversible once the session is terminated.
- No Native Encryption: Although SSL/TLS can be used, POP3 does not inherently offer end-to-end encryption, necessitating additional security measures.
The Balanced View: Is POP3 Right for You?
Choosing between POP3 and other email protocols ultimately hinges on your specific requirements. If you seek offline access and are mainly using a single device for email, POP3 could be the right fit. However, if you require advanced functionalities or need to access your emails from multiple devices, alternatives like IMAP may be more suitable.
By understanding both the advantages and disadvantages of POP3, you are better equipped to make an informed decision that aligns with your email handling needs.
Security Concerns and Measures
When it comes to email protocols like POP3, security isn’t something to be taken lightly. While POP3 has been around for years and has stood the test of time, it also comes with its set of security vulnerabilities and challenges. Understanding these, along with the measures available to mitigate them, can be invaluable.
Vulnerabilities
- Plain Text Authentication: In its basic configuration, POP3 transmits usernames and passwords in plain text, leaving them exposed to eavesdropping.
- Lack of End-to-End Encryption: While SSL/TLS can secure the connection between client and server, POP3 does not offer native end-to-end encryption for email contents.
- Server-Side Risks: Since emails are downloaded and deleted from the server, a compromised server can result in the loss of unread or unsaved messages.
Mitigation Measures
- SSL/TLS: Enabling Secure Sockets Layer or Transport Layer Security ensures encrypted data transmission between the client and server.
- APOP: Authenticated Post Office Protocol can be used as an alternative to plain text authentication. It employs MD5 hashing to protect credentials.
- Firewalls and Intrusion Detection Systems (IDS): Deploying these can alert administrators about any suspicious activities related to your email services.
- Regular Software Updates: Keeping your email client and server software up-to-date ensures that you benefit from the latest security patches.
- Two-Factor Authentication (2FA): Although not natively supported by POP3, some email services offer 2FA as an extra layer of security when logging in.
By taking a multi-faceted approach to security, you can make your POP3-based email system far more robust and secure, safeguarding both your data and your peace of mind.
References & Further Reading
- RFC 1939 – “Post Office Protocol – Version 3”: An in-depth technical overview of POP3, authored by the Internet Engineering Task Force (IETF). (Read More)
- “Email Security with Cisco IronPort” by Chris Porter: A book focusing on email security that covers POP3 and other protocols. (Read More)
- “The Art of Email Security: Offers a simple approach to security measures for email protocols, including POP3. (Read More)
- “Email Architecture, Design, and Implementations” by Kevin Thomas: This book discusses the architecture of email services and protocols, including POP3, and suggests best practices for configuration and security. (Read More)
By diving into these resources, you can deepen your understanding of POP3, its security concerns, and the broader landscape of email protocols.