Remote Authentication Dial-In User Service (RADIUS) is a cornerstone protocol for managing network access. It underpins the security and management of user authentication, authorization, and accounting in a wide range of networking environments.
This article unpacks the intricacies of RADIUS, exploring its operational mechanisms, applications, and significance in contemporary network management.
Index
- What is RADIUS?
- The Evolution of RADIUS
- How RADIUS Works
- RADIUS Authentication Methods
- RADIUS Authorization and Accounting
- Implementing RADIUS in Networks
- Challenges and Solutions
- References

1. What is RADIUS?
Remote Authentication Dial-In User Service (RADIUS) stands as a pivotal client-server protocol that orchestrates remote access to networks. Its fundamental role is to enable the centralization of authentication, authorization, and accounting (AAA) for network access, thus significantly streamlining the management of user identities and their corresponding access rights. The inception of RADIUS was primarily driven by the requirements of dial-up network services, a testament to its historical significance in the evolution of network access protocols. However, its utility has remarkably transcended those initial applications, now supporting an extensive spectrum of network types ranging from traditional wired to contemporary wireless and broadband infrastructures.
This protocol’s architecture is designed to facilitate a seamless interaction between clients (usually network access servers or devices seeking access) and a central RADIUS server. The server acts as the authoritative source for user authentication data and access policies, making it an indispensable component in the infrastructure of modern networked environments. The essence of RADIUS lies in its ability to consolidate user management processes, which includes verifying identities, granting appropriate access levels, and tracking usage for both security and billing purposes. Its adaptability and scalability have ensured its continued relevance and application in various networking contexts, from small-scale corporate settings to large-scale internet service providers.
2. The Evolution of RADIUS
RADIUS’s journey from a proprietary solution to a widely recognized standard underscores its significance in the realm of network security and management. Conceived and developed by Livingston Enterprises in 1991, RADIUS was initially designed to meet the burgeoning needs of dial-up network access control. Its efficacy and robustness quickly garnered the attention of the broader networking community, leading to its adoption as a de facto standard for remote authentication.
The protocol’s milestone achievement came with its adoption by the Internet Engineering Task Force (IETF), which documented RADIUS as RFC 2865 in the year 2000. This formal recognition not only validated the protocol’s importance but also set the stage for its evolution into a more versatile and secure framework for managing network access. Subsequent enhancements and extensions, driven by the IETF and the networking community at large, have expanded RADIUS’s capabilities, enabling it to address a wider array of security challenges and to adapt to the ever-evolving landscape of network technologies.
These developments have facilitated RADIUS’s application in a diverse range of networking environments, further solidifying its position as a foundational element in the architecture of modern networks. Its evolution reflects the dynamic nature of network security requirements, showcasing the protocol’s ability to innovate and adapt in response to new challenges and technologies.
3. How Radius Works
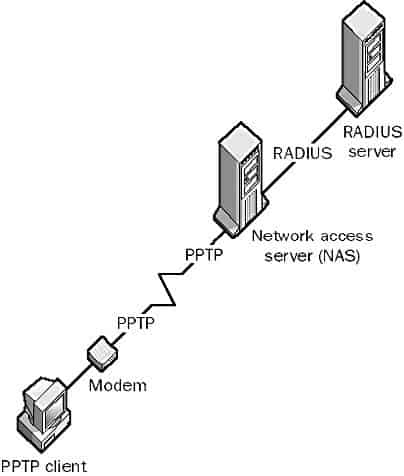
RADIUS is a client/server protocol that centralizes the profile information of dial-up users in a central database on a RADIUS server, which runs special RADIUS software. The RADIUS server is generally separate from the network access server (NAS) that actually allows the client to make a dial-up connection. An RFC-compliant RADIUS server stores all user profile information in a flat-file ASCII database that is accessible by any NAS that needs it to authenticate users.
Some RADIUS servers can also use UNIX password files, Password Authentication Protocol (PAP), Challenge Handshake Authentication Protocol (CHAP), Microsoft Challenge Handshake Authentication Protocol (MS-CHAP), third-party security systems, and Network Information Services (NIS) for authenticating users. This improves the security of remote access to corporate networks through tunneling across the Internet and simplifies administration of remote users. RADIUS servers are also typically used to provide statistics for billing purposes.
In a typical session, a client dials in to a NAS at an Internet service provider (ISP) and submits its credentials, which the NAS reformats as RADIUS packets and forwards to the RADIUS server. The RADIUS server can authenticate the user directly or act as a proxy client to forward the authentication process to some other type of service or security device. Once the RADIUS server authenticates the client, it informs the NAS, which allows the client to complete its connection. All communication between the client and the RADIUS server is encrypted.
RADIUS Protocol is supported by the Internet Authentication Service (IAS).
4. RADIUS Authentication Methods
RADIUS provides a flexible framework for authentication, supporting several methods to verify user identities. This flexibility ensures that network administrators can choose the most appropriate authentication mechanism based on their security requirements and infrastructure capabilities.
Password Authentication Protocol (PAP)
PAP is one of the simplest authentication methods used within the RADIUS framework. It involves the transmission of a user’s credentials (username and password) in plain text from the client to the server. Due to its lack of encryption, PAP is considered less secure and is typically employed in environments where encryption is not deemed necessary or is provided by other means. The primary advantage of PAP lies in its simplicity and broad compatibility with various systems.
Challenge Handshake Authentication Protocol (CHAP)
CHAP provides a more secure alternative to PAP by employing an encrypted three-way handshake between the client and the server. Upon connection, the server sends a challenge to the client. The client responds with a value obtained by hashing the challenge with the user’s password. The server, already in possession of the user’s password hash, performs the same calculation. If the values match, the authentication is successful. CHAP prevents the transmission of the actual password over the network, significantly reducing the risk of credential interception. Additionally, CHAP can be configured to periodically reauthenticate during a session, further enhancing security.
Extensible Authentication Protocol (EAP)
While not exclusively a RADIUS authentication method, EAP is often used in conjunction with RADIUS to support a range of more sophisticated authentication mechanisms, including token-based authentication, smart cards, and biometrics. EAP is particularly useful in wireless networks and point-to-point connections, where it enables flexible and robust authentication strategies beyond traditional username and password schemes.
5. RADIUS Authorization and Accounting
After authentication, RADIUS extends its capabilities to authorization and accounting, further centralizing network access management and providing detailed access control and usage tracking.
Authorization
Once a user is authenticated, RADIUS moves to the authorization phase, where it determines the network resources and services the user is allowed to access. This process involves consulting the user’s profile stored in the RADIUS server, which contains information about their permissions, such as access to specific network segments, bandwidth limitations, or time-of-day restrictions. This granular control allows network administrators to enforce policies consistently and efficiently across the network.
Accounting
RADIUS accounting features offer detailed tracking of user activities on the network. This includes logging session start and end times, the amount of data transmitted and received, user identification, and the IP addresses used during the session. Accounting data is crucial for billing purposes, especially in environments where users are charged based on their network usage. Additionally, this information is invaluable for auditing and monitoring network performance, helping administrators identify usage patterns, potential security breaches, and network abuse.
In summary, RADIUS’s comprehensive approach to authentication, authorization, and accounting makes it an indispensable protocol for managing network access. It not only enhances security through support for various authentication methods but also provides the tools needed for detailed access control and usage monitoring, ensuring both the integrity and efficiency of network services.
6. Implementing RADIUS in Networks
The implementation of RADIUS into network infrastructures is pivotal for enhancing access control and security measures. This process involves a series of strategic steps to ensure seamless integration and optimal performance.
Configuring Network Access Servers (NAS): The initial step involves setting up NAS devices to interact with RADIUS servers. This configuration is crucial for initiating authentication requests and processing responses from the RADIUS server. It includes specifying the RADIUS server’s IP address, shared secret, and other relevant parameters that facilitate secure communication.
RADIUS Server Setup: Deploying a RADIUS server requires installing and configuring RADIUS software on a dedicated machine or virtual environment. This setup entails defining user profiles, access policies, and authentication rules. It’s essential to ensure the server’s security, including updating software regularly and securing network communications.
Integration with Directory Services: For enterprises managing numerous user accounts, integrating RADIUS with existing directory services like LDAP or Active Directory is beneficial. This integration simplifies user management and leverages existing databases for authentication and authorization, enhancing the overall security framework.
Testing and Validation: Before full deployment, conducting thorough testing is crucial to verify the RADIUS implementation’s functionality. This includes testing authentication, authorization, and accounting processes for various user scenarios to ensure the system operates as expected under different conditions.
Monitoring and Maintenance: Continuous monitoring of RADIUS activities is vital for maintaining network security and performance. Regular audits and reviews of authentication logs, access attempts, and system performance help in identifying potential issues and optimizing the RADIUS environment.
7. Challenges and Solutions
Scalability Issues: As networks grow, RADIUS servers may face scalability challenges, struggling to handle an increasing number of authentication requests efficiently. Solution: Implementing load balancing and deploying multiple RADIUS servers can distribute the workload, enhancing the system’s scalability and reliability.
Security Vulnerabilities: Despite its robustness, RADIUS can be susceptible to security vulnerabilities, especially if encryption protocols are outdated or if shared secrets are compromised. Solution: Regularly updating RADIUS software, employing strong encryption methods like TLS, and using dynamic, complex shared secrets can mitigate these risks.
High-Availability Concerns: Ensuring uninterrupted access to network resources is critical. RADIUS server downtime can lead to widespread access issues. Solution: Deploying RADIUS servers in a high-availability configuration, with failover mechanisms, ensures continuous operation even if a server goes down.
Integration Complexity: Integrating RADIUS with diverse network equipment and systems can be complex. Solution: Standardizing configurations and employing flexible RADIUS solutions that support extensive compatibility with various devices and services simplifies integration efforts.
8. References
- RFC 2865 – Remote Authentication Dial-In User Service (RADIUS): This foundational document outlines the RADIUS protocol’s specifications, offering a detailed understanding of its mechanisms and applications.
- Configuring RADIUS with Livingston Server: by Cisco.
- RADIUS Authentication, Authorization, and Accounting: by Microsoft Learn.