In the realm of computer security, especially within Microsoft Windows operating systems, the System Access Control List (SACL) plays a critical role. Distinct from the more commonly known Discretionary Access Control Lists (DACLs), SACLs are integral to auditing and security monitoring, providing a mechanism for administrators to log attempts to access system objects.
This article aims to demystify SACLs, elucidating their purpose, functioning, and how they differ from DACLs. We will delve into the historical evolution of SACLs, tracing their journey from early Windows operating systems to their current form in modern Microsoft environments. By exploring how SACLs have adapted to the changing landscape of network security and auditing needs, we’ll gain a comprehensive understanding of their enduring significance in Windows security architecture.
Table of Contents:
- What is a System Access Control List (SACL)?
- Understanding SACLs and DACLs: A Comparative Analysis
- Historical Evolution of SACLs
- Configuring and Managing SACLs
- SACLs in Action: Real-World Applications
- Challenges and Solutions
- Conclusion
- References

1. What is a System Access Control List (SACL)?
A System Access Control List (SACL) is a feature within Microsoft Windows operating systems designed for security auditing. It is a set of access control entries (ACEs) that specify the security events to be audited for users or system processes attempting to access an object, such as a file or a registry key. Each ACE in a SACL governs the types of access attempts by a user or process that will be recorded in the security log of Windows.
The primary functionality of SACLs revolves around the monitoring and logging of access attempts, rather than granting or denying access (which is the role of DACLs). When a user or process attempts to access an object with a SACL, the system checks the SACL to determine if the attempt should be logged. If so, an entry is made in the security log, detailing the action taken, who initiated it, and whether it was successful or not.
Role in Security Auditing and Monitoring
SACLs are crucial for security auditing and monitoring in a Windows environment:
- Auditing Access Attempts: SACLs enable administrators to track and audit successful and/or failed attempts to access system objects. This helps in identifying potential security breaches or policy violations.
- Enhancing Security Measures: By reviewing the security log entries generated by SACLs, administrators can understand access patterns and identify unusual activities, which is instrumental in strengthening security measures.
- Compliance and Forensics: SACLs are essential for meeting compliance requirements that mandate tracking access to sensitive data. They also play a key role in forensic analysis following security incidents.
2. Understanding SACLs and DACLs: A Comparative Analysis
Differences Between SACLs and DACLs
While both SACLs and DACLs are types of Access Control Lists in Windows, they serve distinct purposes:
- Purpose: DACLs (Discretionary Access Control Lists) are used to define permissions, granting or denying access to an object. SACLs, on the other hand, are used for auditing and monitoring purposes, logging access attempts.
- Function: DACLs determine who can or cannot access an object and what they can do with it (read, write, execute, etc.). SACLs dictate what access attempts should be recorded in the security log.
- Usage: DACLs are more commonly interacted with by users and administrators, as they directly impact access rights. SACLs are typically used in more specialized scenarios, focusing on security auditing and monitoring.
How Each Contributes to System Security
Both SACLs and DACLs are integral to system security, but in different ways:
- DACLs: They are the first line of defense, controlling access and preventing unauthorized users from performing actions on system objects. They are essential for enforcing security policies.
- SACLs: They provide a second layer of security by enabling administrators to track and audit access attempts, regardless of whether they were allowed or denied. This is crucial for detecting potential security breaches and for compliance purposes.
Together, SACLs and DACLs form a comprehensive security model in Windows, addressing both prevention of unauthorized access (DACLs) and monitoring of access attempts (SACLs), thereby ensuring a robust security framework.
3. Historical Evolution of SACLs
Introduction in Early Windows Versions
The concept of System Access Control Lists (SACLs) in Microsoft Windows began to take shape with the introduction of more advanced security models in the early versions of the Windows NT series. These initial implementations laid the groundwork for what would become a sophisticated system of monitoring and auditing access to system resources.
- Windows NT: The era of Windows NT marked the beginning of Microsoft’s focus on enterprise-level security. SACLs in these early versions provided a basic framework for auditing access to files, directories, and other system objects.
Development and Enhancements in Windows NT and Windows 2000
As Windows continued to evolve, the functionality and capabilities of SACLs were significantly expanded:
- Enhanced Auditing Features: With each new release of Windows NT, SACLs became more robust, offering finer control over what types of access attempts were audited.
- Integration with Active Directory: The introduction of Windows 2000 and Active Directory brought new dimensions to SACLs. They were integrated with the domain-based security model, allowing for more centralized and efficient management of audit policies across multiple systems.
- User and Group-Based Auditing: These versions enabled more detailed auditing based on user and group activities, providing administrators with more comprehensive insights into security-related events.
Current Implementation in Modern Windows Operating Systems
In modern Windows operating systems, SACLs have been further refined and integrated into the overall security architecture:
- Advanced Audit Policy Configuration: Starting with Windows Vista and Server 2008, Windows introduced Advanced Audit Policy Configuration, allowing more granular audit policies. This development gave administrators precise control over what actions were audited.
- Event Viewer Enhancements: Modern versions of Windows feature an improved Event Viewer, making it easier to view and analyze audit logs generated by SACLs.
- Security Compliance: The evolution of SACLs aligns with contemporary needs for compliance with various regulatory standards, making them an indispensable tool in security policy enforcement and compliance auditing.
4. Configuring and Managing SACLs
Step-by-Step Guide on Setting Up SACLs
Setting up SACLs in a Windows environment involves a series of steps to ensure that auditing is properly configured for specific objects:
- Enable Auditing Policy: First, access the Local Security Policy or Group Policy Editor and navigate to the audit policy settings. Enable auditing for successful and/or failed access attempts as required.
- Select the Object for Auditing: Choose the file, folder, or other objects that you want to audit. Right-click on the object, and select ‘Properties.’
- Access the Security Tab: In the properties window, navigate to the ‘Security’ tab and click on ‘Advanced.’
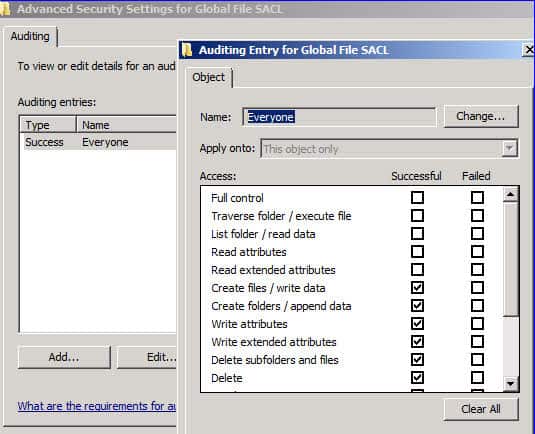
- Edit the SACL: In the Advanced Security Settings, switch to the ‘Auditing’ tab. Here you can view and edit the SACL for the object.
- Add or Modify Auditing Entries: Click on ‘Add’ to create a new audit entry or select an existing entry to modify. Specify the users or groups to be audited and the types of access to be logged (like read, write, delete).
- Apply and Confirm Settings: After configuring the SACL entries, apply the settings. The system will now log the specified activities in the Security Log, viewable in the Event Viewer.
Best Practices for Effective Auditing
- Selective Auditing: Avoid auditing everything, as it can lead to an overwhelming amount of log data. Focus on sensitive or critical objects.
- Regular Review: Regularly review the audit logs to identify unusual activities or access patterns.
- Maintain Audit Logs: Ensure that audit logs are maintained appropriately, considering retention policies and backup strategies for forensic purposes.
- Integration with SIEM Tools: For large environments, consider integrating Windows security logs with Security Information and Event Management (SIEM) tools for advanced analysis and real-time monitoring.
5. SACLs in Action: Real-World Applications
Examples of How SACLs are Used in Enterprise Environments
In enterprise environments, SACLs are leveraged for various purposes:
- Tracking Access to Sensitive Files. Companies use SACLs to monitor access to confidential documents, ensuring that only authorized personnel are viewing or modifying them.
- Regulatory Compliance. Industries under regulatory mandates like HIPAA or GDPR utilize SACLs to audit access to protected data, fulfilling compliance requirements.
- Detecting Potential Breaches. By monitoring failed access attempts, SACLs can help in early detection of unauthorized access attempts, potentially indicating a security breach.
Case Studies Highlighting Their Impact on Security
- Financial Sector: A bank implemented SACLs to monitor access to customer data files. The audit logs helped in identifying an insider threat where an employee was accessing records outside their purview.
- Healthcare Industry: A hospital used SACLs to audit access to patient records. The audit logs were crucial in a legal scenario to prove compliance with patient confidentiality requirements.
6. Challenges and Solutions
Common Issues in Managing SACLs
Managing System Access Control Lists (SACLs) in a Windows environment can present several challenges:
- Overwhelming Volume of Data – One of the biggest challenges is the sheer volume of audit data generated, especially in large organizations with extensive monitoring.
- Complexity of Configuration – Setting up SACLs correctly requires a detailed understanding of both the network environment and the Windows security model, which can be complex.
- Performance Impact – Extensive auditing can impact system performance, as each access event requires logging.
- Data Interpretation and Analysis – The interpretation of audit logs can be challenging, requiring specialized knowledge to distinguish normal activities from potential security threats.
Solutions and Tools for Efficient SACL Management
To address these challenges, several solutions and tools can be employed:
- Audit Policy Optimization – Carefully define audit policies to focus on critical events and objects. This reduces the volume of data and minimizes performance impacts.
- Use of Advanced Security Analytics Tools – Implement advanced security and event management tools that can analyze large volumes of audit data efficiently, identifying patterns and anomalies.
- Regular Auditing and Review Processes – Establish regular processes for auditing and reviewing security logs. This helps in timely identification and response to potential security incidents.
- Leverage Automated Solutions – Utilize automated tools for setting up and managing SACLs, reducing the complexity and potential for human error in the configuration process.
7. Conclusion
System Access Control Lists (SACLs) are a crucial component of the security infrastructure in Microsoft Windows environments. By providing detailed auditing capabilities, they enable organizations to monitor and record access attempts to system resources, playing a key role in security management, compliance, and forensic analysis.
While the management of SACLs can be challenging due to the volume of data, complexity, and potential performance impacts, effective strategies and tools can mitigate these issues, enhancing the security posture of an organization. As Windows continues to evolve, the role of SACLs remains pivotal in the ongoing effort to secure digital assets and maintain robust cybersecurity defenses.
8. References
- “Microsoft Windows Security Essentials” by Darril Gibson.
- “Windows Server 2019 & PowerShell All-in-One For Dummies” by Sara Perrott.
- “Mastering Windows Server 2016” by Jordan Krause.
- “Access Control“, in Network Encyclopedia
- “Access Control List (ACL)“, in Network Encyclopedia