The Security Account Manager (SAM) Database is a cornerstone of user security and management in Windows operating systems. Acting as a secure store for user credentials, SAM plays a pivotal role in ensuring that access to a computer or network is strictly controlled and managed. In this article, we delve into the intricacies of the SAM Database: from its fundamental purpose and architecture to its crucial role in safeguarding user credentials and enforcing security policies. Our journey will not only illuminate the technicalities of the SAM Database but also explore its evolution, current security features, and future trajectory. Ideal for computer science enthusiasts and professionals alike, this comprehensive guide aims to demystify SAM, providing a clear understanding of its importance in the Windows security landscape.
Table of Contents:
- Introduction to the SAM Database
- Historical Perspective: User and Password Management in Early Microsoft Operating Systems
- Architecture of the SAM Database
- Mechanics of User and Password Storage in SAM
- Security Features of the SAM Database
- Cryptanalysis of the SAM Database
- SAM-Related Attacks and Exploits
- Conclusion
- References

1. Introduction to the SAM Database
The Security Account Manager (SAM) Database, integral to Windows operating systems, is where the magic of user security begins. At its core, SAM is a database system that securely stores user credentials – primarily, usernames and passwords. But SAM is much more than a mere repository. It is the fulcrum upon which user access control and security policies pivot, making it a linchpin in Windows security.
SAM operates behind the scenes, typically unnoticed yet indispensable. When a user logs into a Windows system, SAM is at work, validating credentials against its store. This process is not just about matching passwords; it is the first line of defense against unauthorized access. By ensuring that only verified users gain entry, SAM upholds the sanctity of the system’s security.
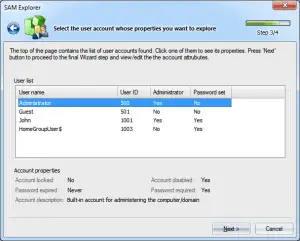
But SAM’s role extends beyond user authentication. It is also a crucial player in enforcing security policies. These policies dictate password complexity, account lockout mechanisms, and other security parameters. In essence, SAM not only checks if a user is who they claim to be but also enforces the rules set to keep the system secure. It’s a delicate balance – maintaining accessibility for authorized users while fortifying against threats.
Furthermore, SAM’s architecture is closely integrated with other Windows components, like the Windows Registry and the Local Security Authority. This integration is pivotal for a seamless security experience, ensuring that security policies and user credentials are consistently managed across the system.
2. Historical Perspective: User and Password Management in Early Microsoft Operating Systems
The journey of user and password management in Microsoft operating systems is a tale of evolving security. In the early days of Microsoft OS, such as MS-DOS and early Windows versions, security was a rudimentary affair. User accounts and passwords were a concept yet to gain the complexity they hold today. These systems primarily functioned in single-user environments with minimal security layers, where the concept of user credentials was either non-existent or very basic.
As Windows evolved, the need for robust security mechanisms became apparent. The advent of networked and multi-user environments in Windows NT heralded a significant shift. It was no longer about securing a single user’s machine; now, the challenge was to protect data in a world of interconnected systems and multiple users. This shift marked the beginning of a more sophisticated approach to user and password management.
The development of the Security Account Manager (SAM) was a response to this growing demand for better security. SAM was introduced as a more secure and scalable way to manage user credentials. It not only stored credentials but also managed them in a manner that was both efficient and secure. The transition to SAM was a turning point, marking Windows’ entry into a new era of security consciousness.
3. Architecture of the SAM Database
The architecture of the SAM database is a marvel of design, balancing security and functionality. At its heart, SAM is a database stored as a part of the Windows Registry, specifically within the System Hive. However, it’s not just any database. Its structure is designed to store sensitive user information, like usernames and hashed passwords, securely and efficiently.
SAM’s interaction with other Windows components is a key aspect of its functionality. It closely works with the Local Security Authority (LSA), a critical component responsible for enforcing security policies on Windows systems. When a user logs in, the LSA interacts with SAM to verify the user’s credentials. This partnership ensures that authentication processes are not just secure but also align with the system’s security policies.
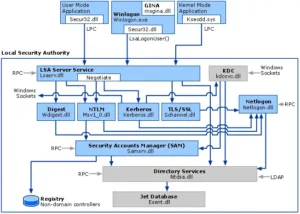
Moreover, SAM’s integration with the Windows Registry is another crucial aspect of its architecture. The Registry acts as the storage backbone for SAM, maintaining the integrity and accessibility of the data SAM holds. This integration allows for a seamless user authentication experience and ensures that user credentials are managed in a unified manner across the system.
4. Mechanics of User and Password Storage in SAM
4.1 Understanding User Account and Password Storage in SAM
At the heart of the SAM database lies its mechanism for storing user accounts and passwords. When a user account is created in Windows, SAM records the account’s details, including the username. However, the password doesn’t get stored in its plain form. This is where the security aspect of SAM comes into play. Instead of storing the actual password, SAM stores a hashed version of it. Hashing is a cryptographic process where the password is transformed into a fixed-size string of characters, which is virtually impossible to reverse-engineer.
4.2 The Role of Hash Functions in Password Security
Hash functions are central to SAM’s password storage mechanism. These functions take the input (in this case, the password) and produce a hash value. This hash value is unique to each password. Even a minor change in the password results in a completely different hash, a property known as the avalanche effect. It’s crucial to understand that these hash functions are one-way – meaning the original password cannot be easily derived from the hash. This makes it extremely difficult for anyone to retrieve the actual passwords from SAM, even if they gain access to the database.
5. Security Features of the SAM Database
5.1 Comprehensive Security Measures in SAM
The SAM database incorporates several layers of security measures to protect user credentials. One of the primary measures is the use of access control. SAM files are stored in a way that they are inaccessible to standard user accounts, and only system-level processes can interact with them directly. This restriction is crucial in preventing unauthorized access to sensitive credential information.
5.2 Encryption Techniques and Security Protocols
In addition to access controls, SAM uses advanced encryption techniques to further secure the stored credentials. The Syskey utility, for instance, adds another layer of encryption to the SAM data, making it more resistant to offline attacks like those involving booting from an alternate OS.
Also, Windows implements various security protocols to regulate access to the SAM database. These include measures like the Account Lockout Policy, which prevents brute force attacks by locking an account after a certain number of incorrect password attempts. Additionally, the implementation of Kerberos protocol in modern Windows environments adds another layer of security for user authentication and authorization.
6. Cryptanalysis of the SAM Database
6.1 Cryptographic Methods in SAM
The Security Account Manager (SAM) database employs a range of cryptographic methods to secure user data. The primary method is the use of hash functions for password encryption. Windows systems traditionally used the LAN Manager (LM) hash and later the more secure NTLM (NT LAN Manager) hash. These hashing algorithms convert plaintext passwords into a scrambled, fixed-length hash value, which is stored in the SAM database. This process plays a crucial role in making passwords resistant to simple recovery attempts.
6.2 Strengths and Vulnerabilities of SAM’s Cryptosystem
While the hashing methods provide a basic level of security, they are not without vulnerabilities. The LM hash, used in earlier versions of Windows, was particularly weak due to its short hash length and lack of complexity, making it susceptible to brute-force attacks. NTLM, while more secure than LM, also has known vulnerabilities, particularly against sophisticated attack techniques like rainbow tables and hash cracking.
Windows addressed these concerns by introducing more robust hashing mechanisms and additional security features like password salting – a process where random data is used as an additional input to the hash function, significantly increasing the complexity of the generated hash. These advancements have strengthened SAM’s cryptosystem, but it’s important to note that no system is entirely invulnerable. Continuous analysis and updates are necessary to maintain robust security against evolving threats.
7. SAM-Related Attacks and Exploits
7.1 Historical Attacks on the SAM Database
Over the years, the SAM database has been a target for various cyberattacks. One notable example is the use of bootable Linux distributions to access SAM files on unencrypted drives. Attackers would boot into an alternate OS and extract the SAM file, using offline methods to crack the password hashes.
Another common attack has been through network intercepts and exploitation of weak password hashes. Tools like L0phtCrack were infamous for exploiting vulnerabilities in the LM hash to recover Windows passwords.
7.2 Case Studies of Significant Breaches
A significant breach involving the SAM database was the 2012 LinkedIn hack. Attackers were able to exploit weak password hashing (unsalted SHA-1) to obtain nearly 6.5 million user passwords, many of which were easily cracked. While not directly involving the Windows SAM, this breach highlighted the importance of robust hashing and salting techniques, principles that are crucial to SAM’s security.
Another notable case was the 2016 Yahoo breach, where attackers stole data associated with at least 500 million accounts. Although it targeted web-based systems rather than SAM directly, this breach underscored the importance of secure password storage and highlighted how vulnerabilities can be exploited to gain unauthorized access to large volumes of sensitive data.

These cases serve as stark reminders of the need for continuous vigilance and advancement in cryptographic methods to protect against sophisticated cyberattacks targeting user credentials.
8. Conclusion
Throughout this article, we have explored the Security Account Manager (SAM) database from its inception to its current form, emphasizing its critical role in Windows security. We began by tracing the evolution of user and password management, leading to the development of SAM in response to the need for more secure systems. The architecture of SAM, with its intricately designed structure and interactions with other Windows components, highlights Microsoft’s commitment to robust security frameworks.
We delved into the mechanics of how SAM stores user accounts and passwords, focusing on the cryptographic methods like hashing and the subsequent security layers added to protect these credentials. The examination of SAM’s cryptosystem revealed both its strengths and vulnerabilities, underscoring the need for continuous advancement in cryptographic techniques.
The historical perspective on SAM-related attacks and exploits demonstrated the real-world implications of vulnerabilities within such systems. These case studies served as potent reminders of the ever-present threats in the cyber landscape and the necessity of maintaining rigorous security protocols.
Understanding the SAM database is crucial for anyone involved in Windows system administration, cybersecurity, and IT management. It is not merely a component of the Windows operating system; SAM is a testament to the ongoing battle between evolving security measures and the ingenuity of cyber threats. A deep understanding of SAM equips professionals with the knowledge to better safeguard systems and data against potential breaches.
9. References
- Russinovich, Mark E., David A. Solomon, and Alex Ionescu. “Windows Internals, Part 1” (7th ed.). Microsoft Press, 2017.
- Microsoft. “Security Account Manager.” Official Microsoft Documentation.
- Scarfone, Karen, and Derrick Dicoi. “Guide to Securing Microsoft Windows XP Systems for IT Professionals: A NIST Security Configuration Checklist.” NIST Special Publication 800-68.
- Solomon, David A., and Mark E. Russinovich. “Microsoft Windows Internals (4th ed.): Microsoft Windows Server 2003, Windows XP, and Windows 2000.” Microsoft Press, 2004.
- RFC 4764 – The EAP-PSK Protocol: A Pre-Shared Key Extensible Authentication Protocol (EAP) Method.
- Swiderski, Frank, and Window Snyder. “Threat Modeling.” Microsoft Press, 2004.

