The Security Reference Monitor (SRM) is an integral part of Microsoft Windows, responsible for enforcing security policies within the operating system. While it has been a cornerstone since the days of Windows NT, the SRM has evolved significantly in its functionality and applicability in newer versions of Windows. This article delves into the SRM’s evolution and its importance in modern Windows operating systems.
Table of Contents
- What is the Security Reference Monitor?
- How Does SRM Work?
- SRM in Windows NT
- SRM Evolution in Modern Windows
- Auditing Capabilities
- Real-world Use Cases
- Frequently Asked Questions
- References
1. What is the Security Reference Monitor?
The Security Reference Monitor (SRM) is a fundamental component that exists in the kernel mode of Microsoft Windows operating systems. Its main responsibility is to act as a gatekeeper for enforcing security policies and access controls within the system. SRM serves as a critical part of the Windows security model, which also includes elements like User Account Control, Windows Firewall, and BitLocker encryption.
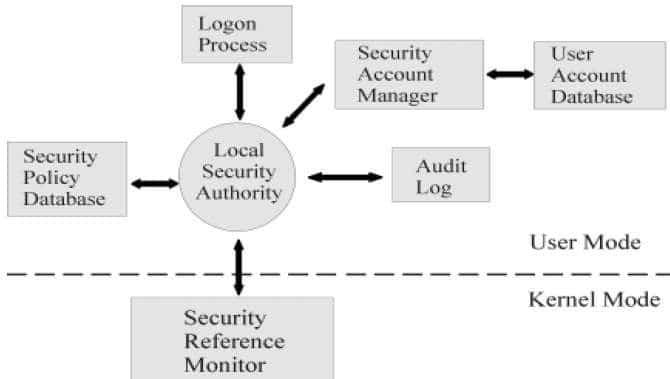
Originally introduced in Windows NT, the SRM’s role has been essential in ensuring that unauthorized users and processes can’t gain access to protected resources within the system. Over the years, the SRM has adapted to new security challenges and now incorporates more advanced features and works in conjunction with other security systems like cloud-based solutions, multi-factor authentication, and biometric verification methods. Whether it’s monitoring access to files, regulating registry changes, or auditing security events, SRM is at the heart of keeping Windows-based systems secure.
2. How Does SRM Work?
To understand the working of the Security Reference Monitor, it’s essential to know a few key terms and mechanisms that it employs. These are the access tokens, Discretionary Access Control Lists (DACL), and Security Identifiers (SIDs).
Access Tokens
An access token is a security object that contains various kinds of data, like the user’s ID, user group memberships, and a range of system and user-defined claims. This token is generated by the Windows security subsystem when a user successfully logs into the system. Every process that the user initiates, either directly or indirectly, carries this token with it, thereby enabling SRM to identify who is responsible for the process.
Here’s a simplified example using pseudocode (python) to show how an access token might be generated:
def generate_access_token(user):
user_ID = get_user_ID(user)
group_IDs = get_group_memberships(user)
other_claims = get_other_claims(user)
return Access_Token(user_ID, group_IDs, other_claims)
DACL and SIDs
A Discretionary Access Control List (DACL) is attached to each secured object in the system. It defines who has what kind of access to that particular object. A DACL contains entries, each of which is called an Access Control Entry (ACE). An ACE has a Security Identifier (SID) that identifies a user or group and specifies the permissions granted or denied for that user or group.
When a process tries to access an object, the SRM goes through the DACL of the object and compares the SIDs against the SIDs in the access token of the process. It uses this information to decide what kind of access to permit or deny.
Here’s a simple example of how this might work in pseudocode (python):
def check_access(access_token, DACL):
for entry in DACL:
if entry.SID in access_token.SIDs:
if entry.permissions == "Deny":
return "Access Denied"
else:
return "Access Granted"
return "Access Denied"
By ensuring that each process’s access token matches the appropriate SIDs in an object’s DACL, the SRM can effectively control access to resources, thus fulfilling its role as a security watchdog.
3. SRM in Windows NT
In its initial incarnation, the Security Reference Monitor (SRM) was introduced in the early days of the Windows NT operating system. Back then, SRM was designed to implement rudimentary security measures, mostly focusing on file and process access control. Its primary goal was to secure local resources and act as a gatekeeper to prevent unauthorized access.
With its simple but effective DACL and access token mechanisms, SRM laid the foundation for the modern, sophisticated security systems we see today in later Windows versions. It was a significant step forward at a time when networked computers were becoming commonplace in businesses, yet robust security solutions were still in their infancy.
4. SRM Evolution in Modern Windows
The SRM has undergone significant evolution since the days of Windows NT, particularly in the context of Windows 10 and Windows 11.
Enhanced Security Features
The first thing to note is the inclusion of advanced security features, such as multi-factor authentication (MFA) and biometric data integration, including facial recognition and fingerprint scanning. These mechanisms work in tandem with SRM, offering an extra layer of security that goes beyond traditional password-based methods.
Cloud Integration
In Windows 10 and Windows 11, SRM is increasingly integrated with cloud-based solutions like Microsoft Azure. This allows the SRM to make real-time decisions based on analytics and threat detection systems that operate in the cloud, significantly improving its ability to adapt to new security challenges.
Virtualization-Based Security
The SRM now benefits from hardware-assisted security features such as Virtualization-Based Security (VBS), isolating sensitive processes from the rest of the system to prevent attacks like pass-the-hash and credential scraping.
Configurability and Granular Control
Modern versions of Windows provide more granular control over the security settings, with policies that can be tailored to meet the specific needs of enterprises, something that was missing or hard to implement in the days of Windows NT. Administrators can set up elaborate rules that decide what kinds of access different kinds of users can have to various resources.
5. Auditing Capabilities
Auditing is another critical role of the Security Reference Monitor. SRM ensures that all attempted access to secured objects and system events are logged if auditing is enabled and configured in the local security policy. These logs are invaluable when it comes to troubleshooting, forensic investigations, and compliance with regulatory requirements.
In modern Windows systems, auditing has become even more advanced. It can now be tied to real-time alerts, enabling immediate action in the event of suspicious activity. Plus, these logs can be integrated with enterprise-wide security information and event management (SIEM) systems for more in-depth analysis and long-term data storage.
Through auditing, SRM plays a vital role in achieving comprehensive security, providing both preventive measures through access control and detective measures through logging and monitoring.
6. Real-world Use Cases
The Security Reference Monitor is ubiquitous in real-world scenarios where Windows-based systems are deployed. Here are some typical use cases:
Enterprise Networks
In large corporate networks, SRM ensures that only authorized employees can access sensitive data stored on network drives or internal applications. It also provides auditing capabilities for compliance with various regulations like GDPR, HIPAA, or SOX.
E-commerce Platforms
For Windows servers hosting e-commerce platforms, SRM plays a critical role in securing customer data and financial transactions. Its auditing features can trace any unauthorized access attempts, thus serving as a deterrent against internal and external threats.
Public Sector
Government institutions and public organizations often have strict security and auditing requirements. SRM helps in ensuring only authorized personnel can access classified or sensitive information.
Remote Work Environments
With the growing trend of remote work, SRM helps ensure that only authorized remote connections are established, and data exchange occurs in a secure environment.
7. Frequently Asked Questions
1. Is SRM exclusive to Windows-based systems?
Yes, the Security Reference Monitor is a Windows-specific component, although similar functionalities might exist in other operating systems under different names.
2. How does SRM differ from a firewall?
While both are security components, SRM is more focused on access control within the system, whereas a firewall primarily guards against external threats coming from the network.
3. Can SRM settings be customized?
Yes, in modern versions of Windows, you can tailor SRM settings via Group Policies and the Local Security Policy editor.
4. Is SRM fail-proof?
While robust, no security measure can be considered entirely fail-proof. It’s crucial to keep the operating system and security policies up-to-date to safeguard against new threats.
5. Does enabling SRM auditing affect system performance?
While auditing does consume some system resources, the impact is generally minimal and is often outweighed by the benefits of having detailed access logs.
8. References
- “Security Reference Monitor – Windows Internals, 7th Edition,” Mark E. Russinovich, David A. Solomon, and Alex Ionescu.
- “Windows Security Basics,” Microsoft Official Documentation.
- “Introduction to Windows Security,” Journal of Cybersecurity, Vol. 5, Issue 3.
- “Windows Server 2019 Inside Out,” Orin Thomas.