Welcome to a thorough guide on the Transmission Control Protocol (TCP). In simple terms, TCP is the communication protocol that ensures the reliable delivery of your data across the internet. In this article, we’ll walk you through not just what TCP is, but also dive into its rich history, inner workings, its symbiotic relationship with the Internet Protocol (IP), and much more. Let’s get started.
Table of Contents
- What is the Transmission Control Protocol (TCP)?
- The History of TCP Protocol
- How the TCP Protocol Works
- TCP and IP: A Dynamic Duo
- TCP Segment Structure
- Security Considerations
- Additional Features and Capabilities
- Conclusion
- References
1. What is the Transmission Control Protocol (TCP)?
The Transmission Control Protocol, commonly referred to as TCP, serves as a foundational pillar for data communication across computer networks worldwide. As part of the Internet Protocol (IP) suite, TCP specializes in enabling reliable, ordered, and error-checked delivery of data. This ensures that when you send an email, download a file, or stream a movie, each packet of data arrives intact, in sequence, and without errors.
Key Features
- Reliable Transmission: One of the defining traits of TCP is its reliability. When a packet of data is sent, the sender expects an acknowledgment (ACK) from the recipient. If the ACK is not received within a predetermined time, the packet is retransmitted.
- Ordered Delivery: TCP numbers each data packet it sends. This numbering allows the recipient to reassemble the data in the correct order, even if the packets arrive out of sequence.
- Error-Checking: Before sending and after receiving a packet, TCP performs an error check using a checksum. If a packet arrives with an error, it is discarded, and an automatic request for retransmission is triggered.
- Congestion Control: TCP dynamically adjusts its transmission rate in response to network congestion, thus avoiding unnecessary load and enhancing overall network performance.
By knitting these features together, TCP ensures that your online interactions, whether simple or complex, are conducted with the highest level of integrity and reliability.
2. The History of TCP Protocol
The Transmission Control Protocol has a storied history that charts the rise of the digital age itself. Conceived in the early 1970s, TCP was part of a larger project funded by the United States Department of Defense and spearheaded by computer scientists Vint Cerf and Bob Kahn.
ARPANET Origins
The original model was first implemented in the ARPANET—the precursor to the modern internet. The primary goal was to create a robust, fault-tolerant, and adaptable network protocol. TCP was initially designed to fulfill both the roles of data transportation and routing, which are now individually handled by TCP and IP respectively.
TCP/IP Split
The TCP/IP model as we know it came into existence in 1978 when the functionality was split into two separate protocols: TCP for reliable communication and IP for routing. This separation allowed for more flexibility and scalability, and it set the groundwork for the explosive growth of the Internet.
Standardization and Adoption
In 1981, the first official specification of TCP was published as RFC 793, establishing it as a standard. Since then, it has undergone numerous revisions and enhancements, but the core principles remain the same.
Global Reach
Over the decades, TCP has grown from a specialized protocol used by a handful of research institutions to a global standard that underpins the majority of internet communication today. Whether you’re sending an email in New York or streaming a video in Tokyo, chances are, TCP is making it happen seamlessly.
By tracing the history and evolution of TCP, one gains a deeper appreciation for how this protocol has continually adapted to meet the growing demands of an ever-expanding digital landscape.
3. How the TCP Protocol Works
The Transmission Control Protocol (TCP) works by establishing a reliable “pipe” between two network endpoints, commonly known as sockets. This pipe acts as a two-way communication channel that ensures data is reliably transmitted and received. Here’s a breakdown of the steps involved:
TCP Handshake
Before any data can be exchanged, both the sender and the receiver must agree to communicate. This agreement is established through a process known as the “TCP handshake.”
- SYN: The initiating socket sends a packet with the SYN (Synchronize Sequence Number) flag set to the receiving socket.
- SYN-ACK: Upon receiving the SYN packet, the receiving socket replies with a packet that has both SYN and ACK (Acknowledgment) flags set.
- ACK: Finally, the initiating socket sends an ACK packet back to the receiving socket to acknowledge the established connection.
At this point, the TCP connection is considered established, and data can begin to flow between the two sockets.
Data Transfer
During data transfer, each packet of data is sequentially numbered, which helps the receiving socket reassemble the data in the correct order. Packets are also acknowledged by the receiver, giving the sender the assurance that the data has reached its intended destination.
Flow Control
TCP incorporates flow control mechanisms, such as window scaling, to prevent fast senders from overwhelming slow receivers.
Connection Termination
Once the data transfer is complete, the connection is terminated using a similar handshake process involving FIN (Finish) flags.
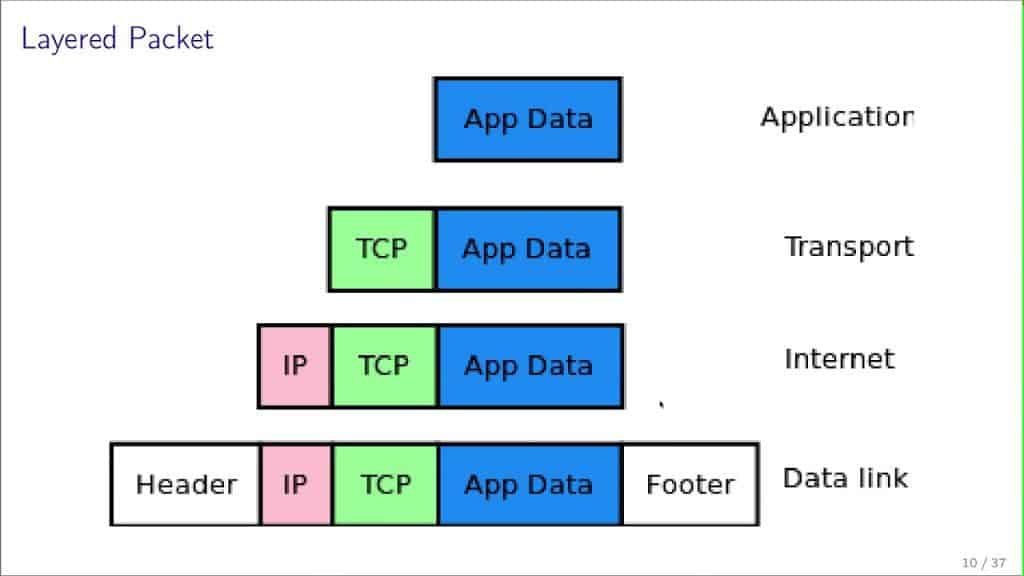
4. TCP and IP: A Dynamic Duo
While TCP ensures reliable and orderly data transfer, the Internet Protocol (IP) focuses on routing packets of data from the source to the destination. Together, they create the TCP/IP protocol stack, the backbone of virtually all modern network communications.
Layering
In the OSI model, TCP operates at the Transport layer, while IP operates at the Network layer. These layers work in tandem but are responsible for different aspects of the communication process:
- TCP: Takes care of segmenting the data, ensuring reliable delivery, and maintaining the order of the segments.
- IP: Deals with the routing and forwarding of packets, essentially getting them from Point A to Point B.
IP’s Role
IP’s primary role is to provide a way to uniquely identify each node in the network through IP addresses. It does not concern itself with the state or reliability of the connection, which is where TCP steps in.
Cohesion and Flexibility
One of the reasons the TCP/IP model is so powerful is its flexibility. TCP can be used with other network protocols, and IP can be used with other transport protocols. However, when used together, they offer a balance of reliability and efficiency.
Ubiquity
The TCP/IP model has become the standard for internet communications and is used in nearly every internet-connected device. It’s the protocol of choice for everything from small local networks to the massive, sprawling architecture of the World Wide Web.
5. TCP Segment Structure
A TCP segment is a standardized bundle of data that travels between the sender and receiver during a TCP communication session. Understanding its structure helps to comprehend how TCP achieves its goals of reliability, ordering, and data integrity. A TCP segment consists of a header and a data section.
Header Fields
The TCP header contains various fields that control different aspects of the communication:
- Source Port and Destination Port: These 16-bit fields identify the endpoints of the connection.
- Sequence Number: A 32-bit field that specifies the order of the data being sent.
- Acknowledgment Number: If the ACK flag is set, this 32-bit field contains the value of the next sequence number that the sender is expecting.
- Data Offset: Indicates the length of the TCP header, which is necessary since the header can vary in length.
- Flags: A set of flags such as SYN, ACK, FIN, and others that indicate the purpose of the segment.
- Window Size: Specifies the size of the receive window, which is used for flow control.
- Checksum: A 16-bit field for error-checking of the header and data.
- Urgent Pointer: If the URG flag is set, this 16-bit field indicates the offset where the urgent data ends.
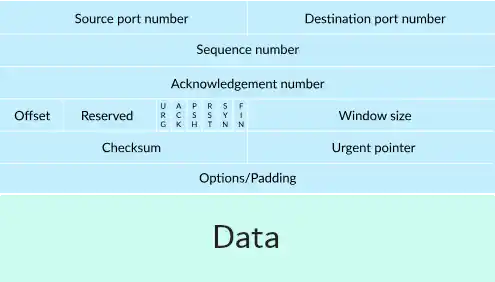
Data Section
Following the header, the data section contains the actual data being transferred. Its size can range from 0 bytes to a maximum defined by the Maximum Segment Size (MSS), which is negotiated during the connection setup.
6. Security Considerations
While TCP is robust and reliable, it is not inherently secure. Various types of attacks target the TCP layer, and certain vulnerabilities need to be managed.
SYN Flood Attacks
An attacker can exploit the TCP handshake process to initiate a SYN Flood. In this attack, the attacker sends numerous SYN packets but does not complete the handshake, exhausting server resources.
IP Spoofing
In IP spoofing attacks, the attacker sends packets that appear to come from a trusted IP address. This can sometimes be used to bypass IP-based security measures.
Sequence Prediction
If an attacker can predict the sequence numbers in a TCP stream, they can inject malicious packets into the data stream. Modern TCP implementations use complex algorithms for generating sequence numbers to mitigate this risk.
Man-in-the-Middle Attacks
Attackers can also intercept TCP packets in transit and either observe or manipulate the data. Secure versions of TCP, like TCP/IPsec and Transport Layer Security (TLS), can help protect against this type of attack.
Best Practices for Security
- Firewalls: Can filter out malicious or unwanted traffic.
- TCP/IPsec: Provides an extra layer of security by encrypting the TCP packets.
- Rate Limiting: Helps to mitigate issues like SYN flood attacks by limiting the rate of incoming connection requests.
- Patching and Updating: Always keep your systems updated with the latest security patches.
7. Additional Features and Capabilities
TCP isn’t just about reliable data delivery; it also offers an array of features that make it versatile and adaptable to varying network conditions and requirements.
Multiplexing
TCP supports multiplexing, allowing multiple applications to send and receive data over a single TCP connection simultaneously. This is achieved through the use of different port numbers for different services.
Nagle’s Algorithm
Designed to improve efficiency, Nagle’s Algorithm helps reduce network congestion by combining smaller messages into larger segments before transmission. This is particularly useful for applications that send data in tiny bursts.
Selective Acknowledgment
Instead of acknowledging data receipt packet by packet, TCP’s selective acknowledgment feature allows the receiver to acknowledge non-contiguous blocks of data, which can significantly improve performance in case of packet loss.
Fast Retransmit and Recovery
These features work together to speed up the retransmission of lost packets and to help recover a TCP connection from packet loss or other errors without resorting to a full-scale timeout.
Quality of Service (QoS)
Though not a part of TCP itself, Quality of Service can be integrated into TCP/IP networks to provide different priority to different types of traffic, thus ensuring that critical applications get the bandwidth they need.
By exploring these additional features, you’ll realize how TCP is not just a one-trick pony; it’s a protocol designed to meet a wide range of network requirements and challenges.
8. Conclusion
TCP is not just a protocol; it’s the underlying heartbeat of most internet communications today. From its origins in the 1970s to its current omnipresent status, TCP has demonstrated unparalleled adaptability and resilience. Understanding its core functions, segment structure, security considerations, and additional features gives you a window into the sophisticated engineering that ensures our digital interactions are both seamless and reliable. As technology continues to evolve, TCP is likely to adapt and grow, further cementing its role as a cornerstone of digital communication.
9. References
- Postel, J. “Transmission Control Protocol,” RFC 793, September 1981.
- Allman, M., Paxson, V., Stevens, W. “TCP Congestion Control,” RFC 2581, April 1999.
- Ramakrishnan, K. K., Floyd, S. “A Proposal to add Explicit Congestion Notification (ECN) to IP,” RFC 3168, September 2001.
- Jacobson, V., Braden, R., Borman, D. “TCP Extensions for High Performance,” RFC 1323, May 1992.
- Kent, S., Atkinson, R. “Security Architecture for the Internet Protocol,” RFC 2401, November 1998.
- “Understanding TCP/IP,” Cisco Systems Inc., Networking Academy Program, 3rd Edition, 2005.
- “The Illustrated Network,” Walter Goralski, 2009, Elsevier Inc.